The cyber kill chain helps understand and predict different stages of a cyberattack. Knowing how hackers work enables a company to select the right tools and strategies to limit breaches, respond to in-progress attacks, and minimize risks.
This article explains the role of cyber kill chains in cybersecurity. We examine every step of an attack and show why kill chains are vital to defense strategies.
What is a Cyber Kill Chain?
A cyber kill chain is a security model that outlines the phases of a cyberattack. A kill chain covers all the stages of a network breach, from early planning and spying to the hacker’s final goal.
Understanding the stages of an attack enables companies to plan the tactics for preventing and detecting malicious intruders. A cyber kill chain helps prepare for all common online threats, including:
- Ransomware attacks.
- Network breaches.
- Data thefts.
- Advanced persistent attacks (APTs).
Read about the different types of cyberattacks and incorporate them into your kill chain planning.
The term “kill chain” has a military background. The original concept defined the structure of an army operation and included:
- The identification of the target.
- The force dispatch towards the target.
- The order to strike at the target.
- The elimination of the target.
Another term for the cyber kill chain is the cyber-attack chain.
7 Stages of a Cyber Kill Chain
The seven phases of the cyber kill chain are the different steps of a successful attack. A security team has a chance to stop attackers at every stage, but a company should ideally identify and stop threats in the first half of the cyber kill chain.
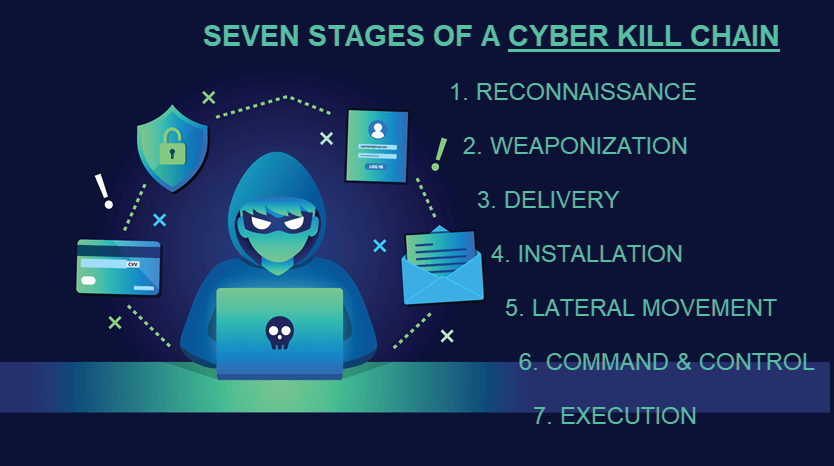
Stage 1: Reconnaissance
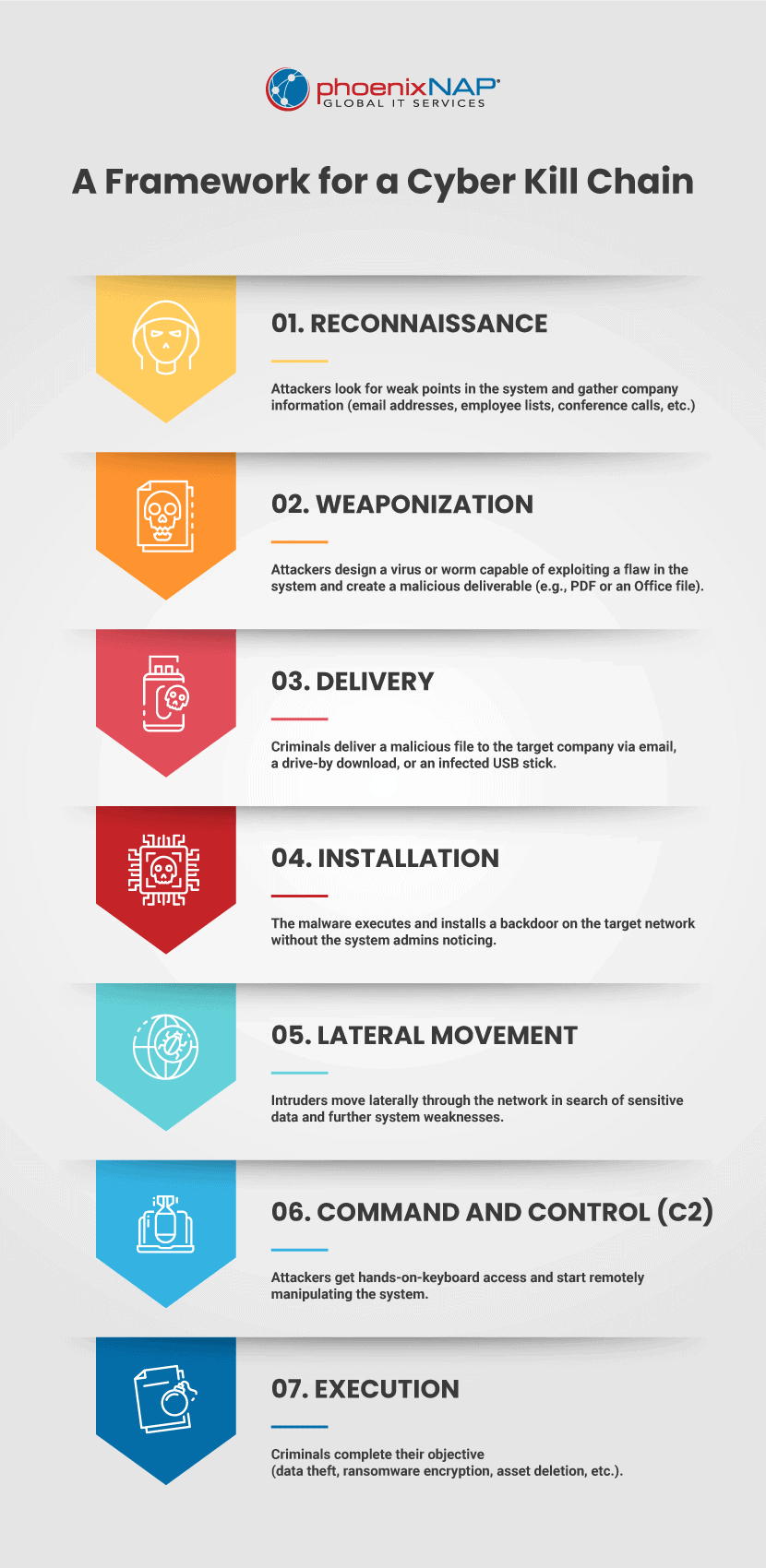
The attacker gathers the necessary information during the reconnaissance step. Hackers select the victim, conduct in-depth research of the company, and look for weak points in the target network.
Learn what vulnerability assessment is and what are the right vulnerability assessment scanning tools to remove weaknesses from your systems.
There are two types of reconnaissance:
- Passive reconnaissance: A hacker searches for information without interacting with the target. The victim has no way of knowing or recording the attacker’s activity.
- Active reconnaissance: A hacker gains unauthorized access to the network and engages with the system directly to gather information.
During this step, attackers assess the following aspects of a system:
- Security vulnerabilities and weak points.
- The possibility of employing an insider accomplice.
- Tools, devices, verification protocols, and user hierarchy.
A common tactic during reconnaissance is to gather employee email addresses and social media accounts. This information is useful if the attacker decides to use social engineering to access the network.
Defensive measures for the reconnaissance stage:
- Set up firewalls to reinforce perimeter security.
- Monitor points of entry and visitor logs for suspicious behavior.
- Ensure employees report suspicious emails, calls, and social media messages.
- Prioritize protecting individuals and systems that are prime targets for reconnaissance.
- Limit the amount of publicly available company data.
Stage 2: Weaponization
The attacker team found a weak point in the system and knows how to create an entry point. The criminal team now designs a virus or a worm to target the weakness. If attackers found a zero-day exploit, they typically work fast before the victim discovers and fixes the vulnerability.
Once malware is ready, hackers typically place malicious software in ordinary documents such as a PDF or an Office file.
Defensive measures for the weaponization stage:
- Run security awareness training to help employees recognize weaponization tests.
- Analyze malware artifacts to check for suspicious timelines and similarities.
- Build detection tools for weaponizers (automated tools that couple malicious software with exploits).
Stage 3: Delivery
Criminals launch the attack into the target environment. The infection methods vary, but the most common techniques are:
- Phishing attacks.
- Infected USB devices.
- Exploiting a hardware or software flaw.
- Compromised user accounts.
- A drive-by download that installs malware alongside a regular program.
- Direct hacking through an open port or other external access point.
The goal of this step is to breach the system and silently establish a foothold. A popular tactic is to launch a simultaneous DDoS attack to distract the defenders and infect the network without alarming security controls.
Defensive measures for the delivery stage:
- Protect from phishing attacks.
- Use patch management tools.
- Flag and investigate changes to files and folders with file integrity monitoring (FIM).
- Monitor for strange user behavior such as odd login times or locations.
- Run penetration tests to identify risks and weak points proactively.
These 17 penetration testing tools help find and close security gaps before intruders breach the network.
Stage 4: Installation
Malicious software is inside the system, and admins are unaware of the threat. The fourth step of the cyber kill chain is when the malware installs on the network.
Once the malware installs, intruders get access to the network (a.k.a. a backdoor). Now with open access, intruders are free to:
- Install the necessary tools.
- Modify security certificates.
- Create script files.
- Look for further vulnerabilities to get a better foothold before starting the main attack.
Keeping their presence secret is critical for attackers. Intruders typically wipe files and metadata, overwrite data with false timestamps, and modify documents to remain undetected.
Defensive measures for the installation stage:
- Keep devices up to date.
- Use anti-virus software.
- Set up a host-based intrusion detection system to alert or block common installation paths.
- Conduct regular vulnerability scanning.
Stage 5: Lateral Movement
Intruders move laterally to other systems and accounts on the network. The goal is to gain higher permissions and reach more data. Standard techniques during this stage are:
- Exploiting password vulnerabilities.
- Brute force attacks.
- Credential extraction.
- Targeting further system vulnerabilities.
Defensive measures for the lateral movement stage:
- Implement Zero Trust security to limit the reach of compromised accounts and programs.
- Use network segmentation to isolate individual systems.
- Eliminate the use of shared accounts.
- Enforce password security best practices.
- Audit all suspicious activities of privileged users.
Stage 6: Command and Control (C2)
Complex, APT-level malware requires manual interaction to operate, so attackers need keyboard access to the target environment. The last step before the execution phase is to establish a command-and-control channel (C2) with an external server.
Hackers typically achieve C2 via a beacon over an external network path. Beacons are usually HTTP or HTTPS-based and appear as ordinary traffic due to falsified HTTP headers.
If data exfiltration is the attack’s goal, intruders start placing target data into bundles during the C2 phase. A typical location for data bundles is a part of the network with little to no activity or traffic.
Defensive measures for the command-and-control stage:
- Look for C2 infrastructures when analyzing malware.
- Demand proxies for all types of traffic (HTTP, DNS).
- Continuously scan for threats.
- Set intrusion detection systems to alert on all new programs contacting the network.
Managed Detection and Response (MDR) provides the agility to identify and react to cyber threats in real-time.
Stage 7: Execution
Intruders take action to fulfill the attack’s purpose. Objectives vary, but the most common goals are:
- Data encryption.
- Data exfiltration.
- Data destruction.
Immediately before an attack starts, intruders cover their tracks by causing chaos across the network. The goal is to confuse and slow down the security and forensics team by:
- Clearing logs to mask activity.
- Deleting files and metadata.
- Overwriting data with incorrect timestamps and misleading information.
- Modifying vital data to appear normal even if there is an attack.
Some criminals also launch another DDoS attack to distract the security controls while extracting data.
Defensive measures for the execution stage:
- Create an incident response playbook that outlines a clear communications plan and damage assessment in case of an attack.
- Use tools to detect signs of ongoing data exfiltration.
- Run immediate analyst responses to all alerts.
What is an Example of a Cyber Kill Chain?
The cyber kill chain example below shows the different stages at which a security team can detect and prevent a custom ransomware attack:
- Step 1: Hackers run reconnaissance operations to find a weakness in the target system.
- Step 2: Criminals create an exploit ransomware program and place it inside an email attachment. Hackers then send a phishing email to one or more employees.
- Step 3: A user makes the mistake of opening and running the program from the inbox.
- Step 4: Ransomware installs on the target network and creates a backdoor.
- Step 5: The program calls to malicious infrastructure and notifies the attacker about the successful infection.
- Step 6: Intruders move laterally through the system to find sensitive data.
- Step 7: Attackers achieve C2 control and start encrypting target files.
Read about common ransomware examples and learn why businesses of all sizes need the right ransomware solutions to protect them.
Drawbacks of the Cyber Kill Chain Model
A cyber kill chain is a framework around which a company can design its security tactics and processess. However, kill chains also have several faults worth pointing out.
A Focus on the Perimeter
The original cyber kill chain appeared in a time when most threats came from outside the organization. In today’s security landscape, treating the perimeter as the primary attack surface has two problems:
- The use of the cloud and micro-segmentation eliminated the concept of castle-and-moat security.
- The insider threats are as dangerous as external ones.
How to fix this issue: Make a well-rounded kill chain by accounting for dangers both within and outside the perimeter. Set up cloud monitoring to ensure your assets are safe both on-premises and in the cloud.
Our article about cloud monitoring tools presents and compares the top 30 options on the market.
Identifying Threats During the First and Second Phases
Reconnaissance and weaponization stages of a cyber kill chain happen outside of the company’s line of sight. Detecting attacks during these stages is difficult. Even if you do notice strange behavior, determining the extent of the threat is impossible.
How to fix this issue: Do not ignore early signs of a potential attack by treating them as a one-time occurrence. Analyze every activity that appears as active reconnaissance or weapon testing.
Lack of Adaptation
The first cyber kill chain appeared in 2011 when Lockheed-Martin created a security model to defend its network. Since then, both the nature and makeup of cyberattacks have changed significantly, leaving some feeling like kill chains cannot prepare a company for advanced threats.
How to fix this issue: Do not create a cyber kill chain and never update the model. A robust kill chain must evolve to remain effective against the latest threats, especially APTs. As your company grows, revise the chain to account for new attack surfaces and potential dangers.
A Backbone of any Security Strategy
While not a security tool or mechanism, a kill chain helps select the right strategies and technologies to stop attacks at different stages. Use a kill chain as a base for an effective security strategy and continue to grow your company without worrying about costly setbacks.
To further protect your business from cyber threats, read our article about cybersecurity best practices.