Maintaining sufficiently high levels of data center security was never more challenging. Facilities today face an all-time high number of threats, so protecting a data center requires a well-thought-out strategy that accounts for all potential risks.
This article explains the basics of data center security and shows what it takes to keep hosting facilities safe from threats. Additionally, we explain how facilities stop both physical and digital dangers, so jump in to get valuable insights on protecting data centers and all their assets (networks, servers, power systems, housed data, etc.).

Check out our Data-Center-as-a-Service (DCaaS) page to see how you can set up an off-site, OpEx-modeled data center with zero upfront costs. You can also learn more about the principles of DCaaS in our Data Center Outsourcing (DSO) article.
What Is Data Center Security
Data center security is a set of policies, precautions, and practices designed to protect facilities and their assets from attacks and unauthorized access. The main goal of data center security is to ensure the confidentiality, integrity, and availability of housed data and services.
Data center security requires an admin to prepare for and prevent a range of security incidents, including:
- Various physical threats (unauthorized access to premises, theft of hardware, vandalism, sabotage, terrorist acts, etc.).
- Natural disasters (earthquakes, floods, hurricanes, wildfires, etc.).
- Various cybersecurity threats (e.g., data breaches, hacking attempts, DDoS attacks, viruses, ransomware, probing, man-in-the-middle attacks, phishing, SQL injections, etc.)
- Fire-related incidents (electrical fires, equipment overheating, power surges, etc.).
- Region-wide and local power outages.
- Unauthorized use of computing resources.
- Data leakage and corruption incidents.
- Various human errors (accidental data deletion, misconfigurations, operational mistakes, etc.).
- Different insider threat scenarios.
- Data exfiltration attempts (either in person or virtually).
Preventing all these threats is no easy task, which is why data center security has three critical needs:
- Clear and complete visibility of users, devices, networks, applications, workloads, and processes.
- High levels of physical and digital segmentation to reduce the scope of unfortunate and malicious incidents.
- A well-rounded threat protection strategy that accounts for all possible physical and virtual risks to the facility.
Check out our articles on data center technology trends and market analysis to stay at the forefront of the hosting industry.
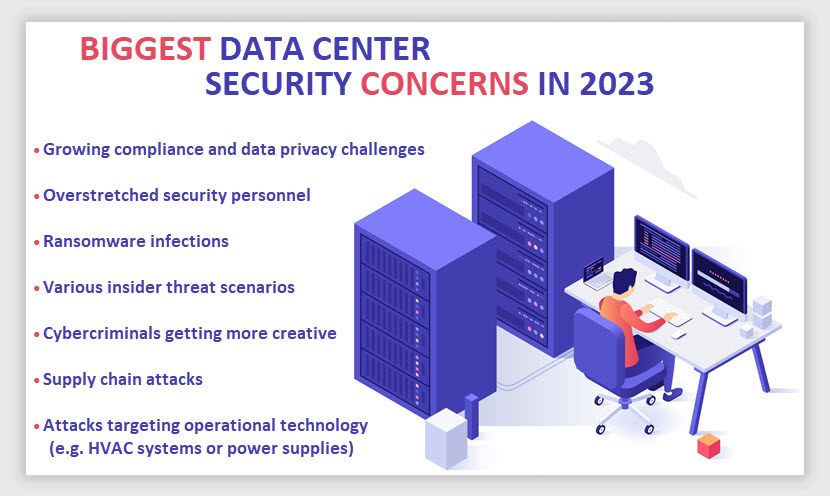
Why Is Data Center Security Important?
Data center security is crucial for several reasons:
- Data protection: A data center stores vast amounts of sensitive and valuable data (PII, financial records, intellectual property, various business files, etc.). Facilities require high levels of security to ensure all that data is safe from unauthorized access, theft, and corruption.
- Protection against cyber threats: Data centers are a prime target for cyber attacks, so investing in adequate cybersecurity measures is a must for any hosting facility.
- Preventing financial losses: Incidents at data centers typically lead to steep financial hits. Each security breach comes with costs of investigation, recovery, legal action, and compensation to affected parties.
- Uptime expectations: Individuals and organizations that use the data center's resources expect a certain amount of service uptime (usually defined in the SLA). Investing in security enables facilities to meet their uptime goals and prevent service disruptions.
- Physical asset protection: Data centers house expensive hardware (servers, networking infrastructure, data storage devices, etc.). Facilities require high levels of physical security to protect these assets from misuse, theft, or damage.
- Business reputation: Suffering a security incident damages the reputation of the data center. Failing to set adequate security measures often leads to a loss of business and credibility.
- Compliance and regulatory requirements: Hosting facilities must adhere to strict compliance standards that require high levels of security. Failing to comply with regulations results in legal penalties and fines.
Security is a vital factor when choosing where to host your data and assets, but not the only one. Learn what else you must consider in our guide to data center selection.
Data Center Security Solutions
It's common to split data center security into two broad categories: physical and virtual protection. A facility requires a high level of both security types to run safely and effectively.
Physical Security Measures
A data center must operate in a secure location, so the area must not be susceptible to natural disasters or be close to risky sites (e.g., airports or power plants). The facility must have limited entry and exit points.
Other standard exterior precautions include:
- High-quality fencing with pointed tip bars that curve outward.
- Minimum windows on the facility.
- Access control points that regulate and monitor people entering and exiting the facility.
- Trained security personnel that guard and patrol the perimeter.
- Surveillance cameras and intrusion detection sensors.
- Barriers that prevent vehicle-based attacks and protect against accidental collisions.
- Locks on all entry points.
Interior security measures typically include the following precautions:
- Trained security personnel.
- Security checkpoints with strict access controls and varying levels of access permissions based on the role of personnel.
- Multi-factor access controls that require something to carry (e.g., a token or magnetic card), something to remember (a PIN code), and a biometric scan (e.g., fingerprint or iris).
- Alarms for various events (e.g., unauthorized access, equipment tampering, physical breaches, etc.).
- High-definition, pan-tilt-zoom (PTZ) cameras that use pattern-based tech to evaluate threats in real time.
- Anti-fire systems equipped with smoke detectors and fire suppression agents.
- Physical barriers (like locked doors and mantraps) that help prevent unauthorized access.
- Turnstiles that prevent two people from trying to enter the facility back-to-back.
The actual hosting equipment also requires high levels of physical security. Here are the usual precautions:
- Locking mechanisms on server racks and cabinets.
- Climate control and sensors that detect changes in temperature and humidity.
- Logging and auditing mechanisms that track access to server racks.
- Tamper-evident seals or stickers on server cabinets.
- Redundant power sources and backup generators.
- Careful cable management to prevent tangling and tripping hazards.
Most principles of data center physical security apply to on-site server rooms, only on a smaller scale.
Should Security Staff Be Visibly Armed with Guns?
Whether data center security personnel should be visibly armed or not has been a longstanding point of debate. Here are the two main arguments for arming the security staff:
- Firearms act as a visual deterrent and may discourage intruders from attempting to breach the premises.
- Armed personnel are ready to respond quickly to potentially severe threats.
Despite these pros, there are significant downsides to arming your security staff. Here are the main arguments against allowing security personnel to carry weapons while guarding a data center:
- Introducing firearms into a facility carries inherent safety risks (e.g., accidental discharge or mishandling of weapons).
- The presence of firearms typically escalates tense situations.
- Armed security creates an intimidating atmosphere that may deter potential clients, visitors, or even employees.
Facilities must perform a comprehensive risk assessment and consider the specific security needs of the facility when deciding whether to arm their guards. In most cases, unarmed personnel combined with surveillance systems, access controls, and emergency response plans is enough to handle incidents effectively.
If you decide to arm your security staff, ensure everyone carrying a weapon undergoes rigorous and ongoing training for responsible handling and use of firearms. Also, keep in mind that regulations in some locations restrict the arming of guards, so ensure your security strategy complies with local laws.

Virtual Security Measures
Virtual security measures focus on protecting digital assets and data within the facility. The primary virtual layers of data center security include:
- Network-level security: Data center admins must control and monitor traffic entering or leaving the network. High levels of network security require investments in different types of firewalls, intrusion detection systems (IDS), network segmentation, DDoS protection, anti-malware tools, and Zero-trust Network Access (ZTNA).
- Application security: This layer focuses on protecting the apps running within the data center. Go-to measures are secure coding practices, 2FA/MFA, application firewalls, runtime protection, and web application and API protection (WAAP).
- Data security: Preventing unauthorized access, theft, or leakage of data requires the combined use of encryption (at rest and in transit), strict access controls, data loss prevention (DLP) mechanisms, and regular data backups (ideally on immutable backups to prevent ransomware infections).
- Identity and Access Management (IAM): IAM enables an admin to ensure users, apps, and services have appropriate permissions and go through proper authentication before accessing data and systems.
- Server monitoring: Effective server monitoring is crucial for identifying and mitigating security threats in real time.
- Honeypots: Honeypots are decoy systems designed to deceive an attacker breaching the network. A honeypot diverts an attacker's attention away from critical systems and enables the security team to analyze the intruder's breach tactics.
- Behavioral analysis: Behavioral analysis tools monitor user and system behavior for abnormal activities indicative of attacks or unauthorized access. Most of these tools rely on machine learning (ML) and artificial intelligence (AI).
- Virtualization security: Facilities that offer cloud computing services must invest heavily in virtualization security (ensuring isolation between virtual machines (VMs), securing hypervisors, preventing VM escape attacks, etc.).
Check out our article on virtual data centers to see how software-defined hosting environments operate and how admins keep them safe from threats.
Data Center Levels of Security
Different data centers have different security precautions based on their tier level. This is a standardized ranking system used to classify facilities based primarily on infrastructure redundancy and availability levels.
In general, a higher tier indicates that the facility has more advanced physical and cybersecurity measures. Here's what to expect from each tier in terms of security:
- Tier 1 data center security: This tier includes basic physical security measures (perimeter fencing, cameras, and limited access controls) and virtual security measures (basic firewalls and anti-malware and virus software). These data centers often have single points of failure and offer minimal redundancy in power and cooling.
- Tier 2 data center security: These facilities have better physical security features (controlled access points, security guards, and stricter visitor policies) and basic monitoring capabilities. However, they lack advanced threat detection and response systems. Tier 2 data centers have improved redundancy in power and cooling, which reduces the risk of downtime.
- Tier 3 data center security: Tier 3 facilities have advanced security precautions, such as intrusion detection and prevention systems (IDPS), security information and event management (SIEM), and robust data protection measures (e.g., regular backups, encryption, secure data destruction, etc.).
- Tier 4 data center security: In addition to tier 3 precautions, tier 4 facilities have state-of-the-art physical security features (biometric access controls, smart video surveillance, 24/7 security personnel, etc.) and advanced threat detection systems with continuous monitoring. These data centers can withstand multiple failures without any service disruption, providing the highest level of fault tolerance.
Our article on data center tiers goes in-depth into what you should expect from different facilities and explains how to use rankings to assess the quality of a data center.

What Are the Best Practices for Data Center Security?
Here are a few best practices data center admins use to further improve security at their facilities:
- Ensure all operating systems, apps, and firmware are up to date with the latest patches to avoid zero-day exploits.
- Perform regular vulnerability assessments to search for flaws in systems and protocols proactively.
- Use an enterprise password management (EPM) tool to ensure all employees and users rely on unique and strong passwords.
- Adopt a zero-trust security model (both for physical and virtual precautions) that requires continuous authentication of every user, device, and app.
- Ensure the security team follows encryption key management best practices.
- Regularly test the data backup and recovery processes to check their effectiveness and look for signs of data corruption.
- Use app whitelisting to prevent unauthorized software from executing within the data center.
- Organize security awareness training that prepares employees for various incidents and teaches them to recognize signs of suspicious activity.
- Prevent lateral movement by always segmenting building systems and Wi-Fi networks from production networks and servers.
- Never take shortcuts with day-to-day server management.
- Maintain detailed logs of all server-related activities.
- Regularly review access control policies to ensure everyone has appropriate access levels.
- Organize occasional penetration tests to see how staff members and systems react to realistic simulations of breach attempts.
- Establish a Security Operations Center (SOC) to improve the team's ability to detect and respond to incidents.
- Define incident response plans to minimize downtime in times of crisis and ensure the data center recovers quickly from disasters.
Our disaster recovery checklist helps create a well-rounded DR plan that minimizes the impact of IT disruptions.
Take Zero Chances with Data Center Security
The main challenge of data center security is that the stakes are incredibly high. Any major incident (ransomware injection, data breach, fire, etc.) has the potential to damage hundreds of businesses that rely on the facility. Instead of risking such dire scenarios, data centers invest a fortune in the security precautions discussed above and take zero chances when preparing for potential threats.



