Data Loss Prevention is critical for any business that captures or stores data. With more and more sensitive data being collected, the consequences of a breach are increasing.
In this article learn, what data loss prevention is, best practices, and how to get started creating a DLP policy.
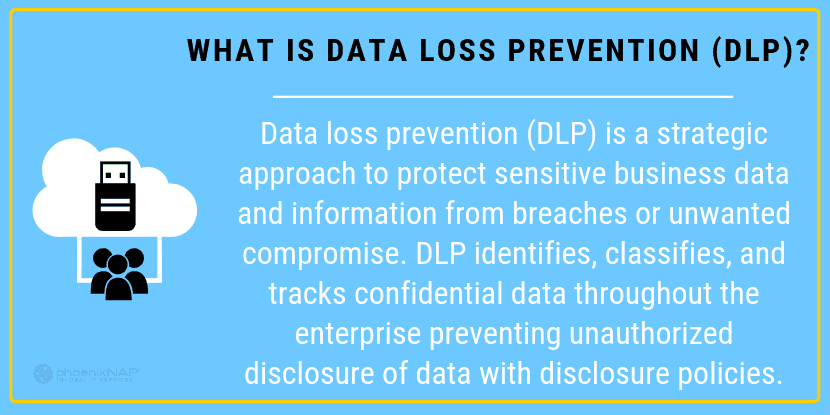
What is Data Loss Prevention (DLP)?
Data loss prevention (DLP) is an approach to protect sensitive business data and information from data breaches or unwanted compromise of sensitive data. DLP identifies, classifies, and tracks confidential data throughout the enterprise preventing unauthorized disclosure of data with disclosure policies.
Data loss happens when a user gets unauthorized access to sensitive information. Data Loss Prevention is a suite of tools and procedures to prevent data loss.
There are three main components to DLP:
- Identify and categorize sensitive data
- Trace the route of data transmission
- Prevent unauthorized access to data
Data Loss Prevention Planning Best Practices
Define an Objective
The objective is the engine that drives the project. You should decide what’s most important. Areas to consider include:
- Protect customer data
- Stay compliant with regulations
- Keep Intellectual Property safe
- Avoid lawsuits and fines over a data breach
Get All Departments On-Board
Some companies have strict, limited budgets. Others might have reluctant leaders who don’t see the value in DLP. If you’re having trouble pitching the importance of a DLP plan, consider these selling points:
- Show how DLP reduces risk
- Show how DLP plans can include policies and technology that improve business processes
- Show how DLP can automate some tasks and reduce expenses
Get to Know Your Vendors
Ask relevant security questions of your vendors. You’ll want to know if software applications are compatible with your business environment. Find out the costs and features for each vendor, and make sure they’re a good fit. Vendors should be able to speak to compliance, partners, and technologies that they use. They should also be able to tell you who controls the DLP program, whether it’s in-house or vendor-managed. Find out staffing requirements and how those will be affected.
Establish Targets
Define an easy-to-achieve target, then roll out the plan to solve it. Success breeds success. A Data Loss Prevention program can be complex and frustrating to staff. Early wins help boost morale, plus helps sell the continuity of the project to decision-makers.
Causes of Data Loss
Data loss and data leakage can be broken down into three main categories. These categories help you develop tools and procedures to protect data.
Negligence
Many data breaches occur because a critical asset wasn’t protected. In many cases, this is simply an error, like a misconfigured firewall, or a MySQL database using the default configuration.
Other times, breaches are related to the budget. Without enough dollars in IT security, professionals may lack the resources to protect data effectively.
A popular attitude among hacker is that “If it’s not locked down, it’s fair game.” It’s a good idea to remember this when evaluating a data protection plan. Anything you ignore or overlook could be used against you.
Infiltration
This is the most common conception of a breach. A criminal attacks your network and gains access. Techniques used to hack into systems include:
- Phishing – In this kind of attack, an email tries to solicit sensitive information or login credentials. Spear-phishing is one type of phishing, in which a specific person is identified and attacked.
- Malware – Attackers try to load malware into the corporate network. Malware could include a computer virus, Trojan horse, rootkits, keyloggers, and other malicious software. Malware can hide in a network, recording data and broadcasting back to its owner.
- Social engineering – An attacker manipulates an employee into granting them access. This could be used in combination with malware. Or, it could merely be an attacker wearing a disguise and asking an employee to open the door.
Insider threats
This is the gut-punch of data breaches. An insider threat or attack is when someone inside a company steals data.
How to Build a Data Loss Prevention Policy
Evaluate current data use
Before enacting sweeping changes, evaluate the ecosystem of your data environment. It’s essential to find out what data is being used, and who’s using it. For example, securing payment card data might sound like a great idea, until sales reps can’t process payments.
Categorize Data Types
A custom solution may be required. Consider using “Employee information,” “Intellectual property,” “Financial information,” and “Customer data” as a starting point. These categories allow you to create different rules to handle different kinds of data.
Monitor Data usage and Transmission
Once categories are established, examine how the data used. Identify storage locations and transmission channels to provide context for data protection strategies.
Start gently
It can be tempting to implement a DLP system right away. The reality is that business data systems can be too complicated for a single sweeping change. A better policy is to tackle easier, obvious targets first to manage the most significant risks while building a culture of data protection.
What Type of Data Loss Prevention is Right for Your Organization?
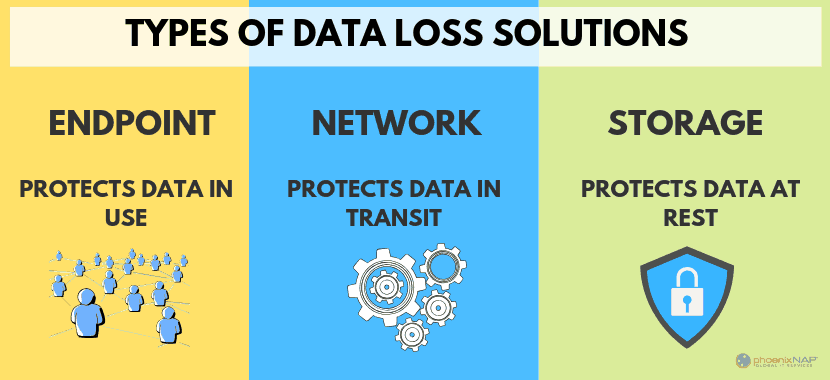
Data loss prevention techniques can be broken into three categories:
- Endpoint – This protects data in use, and devices used to access data. It could be as simple as a terminal or as complex as shadow IT of smartphones and tablets.
- Network –This protects the data during transit. Behavior analysis and traffic monitoring are common tools.
- Storage – This protects data at rest. This governs access to data in storage, whether on NAS drives or the cloud.
Steps to PreventData Loss
Compliance
If your business is regulated, compliance is a critical piece of a DLP plan. Starting at mandatory regulation helps to ensure custom data policies don’t contradict compliance. For example, Healthcare companies must comply with HIPAA compliance. To process credit cards, you need a PCI-DSS compliance plan.
Organize Data by Risk and Vulnerability
To start, identify, and organize data by type. The next step is to analyze each data type. Look at the level of risk each category presents, then their vulnerability to establish a list of targets. Start with the riskiest and most vulnerable data types. Then, implement a set of policies and technology to protect them.
Define User Roles
Users should have clearly-defined roles to make sure that users can only access data that’s necessary for their job. Examples might include a “Sales Agent” job that allows access to payment card data. Another example might be “Senior Technical Support,” which has access to bug reports and engineering fixes. Data can be restricted from specific user roles as well. A Senior Technical Support agent doesn’t usually need access to payment card data.
Involve Key Stakeholders
No one knows the business like the people doing the work. Take time to involve leaders from different parts of the company. They often see vulnerabilities that upper management can overlook and also anticipate problems or conflicts with new policies. Employees are more likely to buy into a new plan if they are involved in developing it.
Create policies, implement technology
It should go without saying that DLP plans should be enacted. If the DLP plan requires a review of all firewall settings, make sure employees are tasked with that job. Create a timeline for buying, testing, and installing new DLP software.
Automate
Humans make mistakes, and our ability to see problems can be limited.
Automating data loss tools and policies helps reduce the risk of human error. Some tasks cannot be automated. Wherever possible, try to create systems that protect data automatically. For example, spam-filtering software can prevent phishing attacks. Users are protected because they never have a chance to see (or be manipulated by) a phishing email.
Educate
Education takes leader involvement to the next step. Leaders who help develop DLP plans already understand the policy. The next step is to train individual team members. A good data loss prevention strategy is to teach what, then why. Explain the new systems and software and how to use it. Then have a conversation about why this change is essential. Help them understand how protecting data is a win for the company and its customers.
Document
Write down a master plan of the DLP solution. Proper documentation is essential for a couple of reasons. First, it helps keep the project on task. Everyone can refer back to the agreements and plan that was made. Second, it helps keep a record of what’s been implemented. The documentation is especially helpful if there are instructions. At a minimum, leave a brief note with the “how” and “why” for each part of the DLP plan.
Measure
Once the DLP plan is in place, check back regularly, and review the progress. Most data loss prevention tools have reporting metrics. Check to see how many intrusion attempts have been blocked. Review server logs to verify that data is being used appropriately.
Delete Unnecessary Data
It can be tempting to hold on to data forever. We never know when we might need it! Old, unused data can be a liability. If server logs are no longer required after seven years, delete them. If you can’t bear to delete them, archive them in long-term, secure storage. That data might seem valuable. But the value can easily be outstripped by its vulnerability. When weighed against the cost of a data breach, old data might not seem quite so important.
DLP Statistics
Cybercrime is big business. Here are a few sobering facts about Data Loss and the consequences.:
- Data loss is estimated to have generated over a half billion dollars profit for cybercriminals in 2018.
- Security breaches increased by 11% in 2018.
- 43% of cyber attacks target small businesses.
- Ransomware statistics show that is costs businesses more than $75 billion per year.
- 83% of IT security professionals have experienced phishing attacks. Source: (Wombat Security)
- It takes an average of 50 days between discovery and reporting of a breach.
DLP is a culture, not a silver bullet
Building a data loss prevention strategy is a critical component for today’s digital businesses.
The landscape of digital crime is continually evolving. A quick, one-and-done solution may be effective today, but obsolete tomorrow. Instead, develop policies as living documents. If a vulnerability is discovered, a flexible and growth-oriented security policy can better adapt to new threats. Eventually, data protection will grow to become a core feature of company culture.