At rest encryption is an essential component of cybersecurity which ensures that stored data does not become an easy target for hackers. As cybercriminals continue to develop more sophisticated methods to reach and steal business info, encrypting data at rest has become a mandatory measure for any security-aware organization.
This article is an introduction to data at rest encryption. Read on to learn about the importance of encrypting static data and see what practices companies rely on to keep stored assets safe.
What is Data at Rest?
Data at rest refers to data residing in computer storage in any digital form. This data type is currently inactive and is not moving between devices or two network points. No app, service, tool, third-party, or employee is actively using this type of info.
At rest is not a permanent data state. As soon as someone requests a file, that data moves across a network and becomes in-transit data. Once someone (or something) starts processing a file, the data enters the in-use state.
Data at rest includes both structured and unstructured data. Some examples of where a company can store data at rest are:
- Hard and SSD drives on PCs and laptops.
- Database servers.
- The cloud.
- At a third-party colocation facility.
- Edge-point devices and portable storage (mobile phones, USBs, tablets, portable hard drives, etc.).
- Network-attached storage (NAS).
Data at rest is a go-to target for a hacker. Static data storage typically has a logical structure and meaningful file names, unlike individual in-motion packets moving through a network. Data at rest also typically contains the company's most valuable and private info, such as:
- Financial documents (past transactions, bank accounts, credit card numbers, etc.).
- Intellectual property (product information, business plans, schematics, code, etc.).
- Contacts.
- Marketing data (user interactions, strategies, directions, leads, etc.).
- Employee and customer personal info.
- Healthcare data.
- Contracts.
- Supply chain info.
While data at rest is static, this type of data actually "moves" around. Companies often replicate files at rest in virtualized environments, back up drives to off-site facilities, allow employees to take laptops home, share data via portable devices, etc.
To maintain the privacy and safety of data at rest, a company should rely on data encryption. Encryption is the process of translating a piece of data into seemingly meaningless text an unauthorized person (or system) cannot decipher.
What is Data at Rest Encryption?
Data at rest encryption is a cybersecurity practice of encrypting stored data to prevent unauthorized access. Encryption scrambles data into ciphertext, and the only way to return files into the initial state is to use the decryption key.
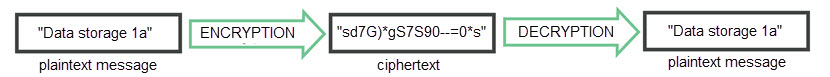
If an unauthorized person accesses encrypted data but does not have the decryption key, the intruder must defeat the encryption to decipher the data. This process is significantly more complex and resource-consuming than accessing unencrypted data on a hard drive.
Encrypting data at rest is vital to data protection, and the practice reduces the likelihood of data loss or theft in cases of:
- A data breach.
- Lost or stolen devices.
- Inadvertent password sharing.
- Accidental permission granting.
- Data leakage.
In most cases, at rest encryption relies on symmetric cryptography. The same key encrypts and decrypts the data, unlike with asymmetric encryption in which one key scrambles data (public key), and the other deciphers files (private key). Security teams typically choose symmetric cryptography when speed and responsiveness are the priority, which is often the case with data at rest.
Unfortunately, data encryption is not only a defensive strategy. Criminals use cryptography to pull off ransomware attacks, a dangerous cyberattack that encrypts business data and forces companies to pay ransom for the decryption key.
Ransomware attacks often lead to permanent data loss even with a robust response plan, which is why many organizations invest heavily in ransomware prevention tactics.
PhoenixNAP's ransomware protection service prevents ransomware via a range of cloud-based solutions. Eliminate the risk of data loss with immutable backups, DRaaS offerings, and infrastructure security solutions.
Encryption at Rest Vs. In-Transit
While encryption at rest and in-transit both rely on cryptography to keep data safe, the two processes greatly differ. The table below outlines the main differences:
| Point of Comparison | ENCRYPTION AT REST | ENCRYPTION IN TRANSIT |
|---|---|---|
| Main purpose | Protect stored, static data. | Protect data moving from one location to another (such as across the Internet, through a private network, or between services). |
| Type of cryptography | Typically relies on symmetric keys to ensure data storage maintains acceptable speed. | Typically uses asymmetric keys for extra protection around data in motion. |
| Main vulnerability | Data storage contains more valuable info than an individual in-transit packet, making these files a worthwhile target for a hacker. | In-transit files are more vulnerable than at-rest data as you cannot reliably prevent eavesdropping when sending messages over the Internet. |
| How it works? | Keeps data encrypted until a person (or system) provides a decryption key required to access data. | Encrypts messages before transmission and decrypts them upon arrival to the destination. |
The two encryption types are not mutually exclusive to each other. Ideally, a company should rely on both encryption at rest and in-transit to keep business data safe.
Types of Data at Rest Encryption
A company can deploy data at rest encryption at four different levels:
- Application-level encryption: The app that modifies or generates data also performs encryption at client workstations or server hosts. This type of encryption is excellent for customizing the encryption process for each user based on roles and permissions.
- Database encryption: The security team encrypts the entire database (or some of its parts) to keep the files safe.
- File system encryption: This type of encryption enables an admin to encrypt only selected file systems (or folders within a file system). Anyone can boot up the device with this encryption but accessing the protected file system(s) requires a passphrase.
- Full disk encryption: This security strategy converts data on the entire hard drive into a nonsensical form. The only way to boot up the device is to provide a password.
Full disk encryption is the most secure form of protecting data on a device. However, you can only use this type of encryption on a new disk as encrypting an existing one wipes the device clean in the process.
Importance of Encryption at Rest
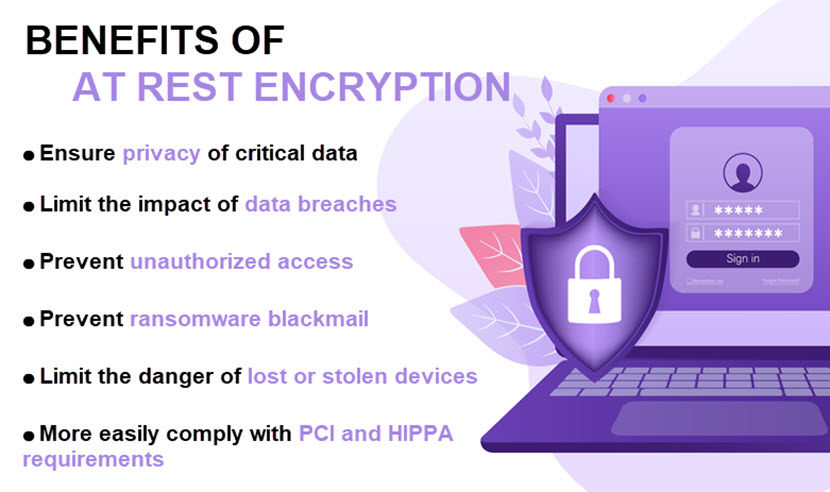
No well-rounded data protection strategy is complete without encryption at rest. A company should protect valuable at-rest data with encryption as this process:
- Blocks unauthorized access to critical data, whether coming from inside or outside of the organization.
- Prevents an intruder from easily identifying, interpreting, and stealing valuable data.
- Limits the blast radius in case of a successful attack.
- Protects the organization if someone steals or loses a storage device.
- Prevents blackmail attempts following data exfiltration.
Encrypting data at rest can also help comply with regulatory requirements. Good examples are the Payment Card Industry Data Security Standard (PCI-DSS) or the Health Insurance Portability and Accountability Act (HIPAA), two regulations that require sound at-rest encryption. While not a necessity for GDPR and CCPA, encryption at rest also helps ensure the privacy of customer data.
Data at Rest Encryption Best Practices
Below is a list of the best practices an organization should follow when planning, implementing, and managing its encryption at rest strategy.
Map and Classify Valuable Data
Before deploying encryption at rest (or any other type of security strategy), you should first map your most sensitive company and customer data. Data classification varies between businesses, but an excellent starting point is to determine:
- The criticality of each piece of data in your possession.
- The types of data your organization keeps.
- The digital location where valuable data resides.
- The physical location of all storage devices.
- All the personnel, apps, and systems that have access to sensitive data.
This analysis helps assess what data requires encryption and what files do not require as high of a protection level. With that info, you can start planning your encryption strategy and align the efforts with your business' unique needs and use cases.
Data classification is a dynamic process that does not end after the first assessment. A company should constantly reevaluate sensitivity levels of data and readjust its encryption strategy accordingly.
Robust Key Management
The encryption strategy is only as reliable and secure as your key management. Keeping keys safe throughout their lifecycle (creation, storage, usage, management, and deletion) is vital, which is why you should implement the following key management best practices:
- Never store encrypted data in the same storage as the corresponding decryption key.
- Rely on a variety of keys for different systems and subsystems.
- Update keys regularly.
- Do not rely on previously used keys.
- Use zero trust security to keep keys safe.
- Store keys on an HSM (hardware security module).
- Never hard-code your keys.
- Have reliable key backups and recovery protocols.
- Centralize encryption key management to make operations more effective, secure, and visible.
Our Encryption Management Platform is an all-in-one EMP solution that enables you to centralize encryption operations and manage all keys from a single pane of glass.
Set Up Confidential Computing
If your organization relies on cloud services and desires to protect data with encryption, you should consider confidential computing. This new model for cloud security expands at rest and in-transit encryptions with data in-use protection, ensuring end-to-end data security.
By encrypting workloads during processing, confidential computing even further reduces the risk of a breach or leak. Some of the main benefits of this strategy include:
- Encryption across the entire data lifecycle.
- Reduced attack surface.
- Minimized risk of outsider and insider threats.
- Better environment controls and greater transparency.
- Improved security in multi-cloud setups.
PhoenixNAP Bare Metal Cloud features Intel SGX-enabled servers and provides a confidential computing solution for deploying at rest, in-transit, and in-use encryption across your cloud infrastructure.
Keep Speed in Mind
Encrypting every piece of data in your organization is not a sound solution. Decrypting data is a process that takes significantly more time than accessing plaintext data. Too much encryption can:
- Slow down operations.
- Impact app performance.
- Make everyday tasks overly complex.
- Seriously impact business scalability and team agility.
Limit the amount of data you encrypt to avoid performance issues. For example, if a database contains sensitive data and non-critical files, you can use selective encryption of database fields (or rows or columns) instead of encrypting all data.
Likewise, you should be sensible with key sizes as large keys can cause issues. For example, if you use AES symmetric encryption, you do not need to use the top AES 256 cryptography for all data. You can instead strategically use faster 128-bit and 192-bit AES for protecting less sensitive but still valuable info.
If speed and agility are of the essence, PNAP's Bare Metal Cloud is the dedicated server platform for you. BMC provides near-instant deployments, adaptable management (through API, CLI, or IaC tools), and various cost optimization features.
Protect Devices with Full-Disk Encryption
While the app, file, and database-level encryption have their uses, the safest practice is to rely on full disk encryption.
Full disk encryption is the most secure strategy as it protects data even if someone steals or loses a device with sensitive info. The need for full-disk encryption becomes even more vital if your company relies on BYOD (Bring Your Own Device) policies.
Do Not Overlook Infrastructure Security
Data at rest encryption is only as secure as the infrastructure that supports the process. Ensure the team runs proper patching of all relevant:
- Servers.
- Networking services (IP addressing, satellite, DSL, wireless protocols, etc.).
- Operating systems.
- Network software (both on-prem and in the cloud).
- Apps for network security.
- Firewalls.
Read about network infrastructure security, an often overlooked yet vital component of secure networking.
A Must for any Well-Rounded Cybersecurity Strategy
With the right tactic and sound key management, a company can use data at rest encryption to lower the likelihood of data breaches and all associated fines and revenue losses. Alongside in-transit and in-use encryption, data at rest encryption should be a cornerstone of your cybersecurity strategy.