Every endpoint (PC, laptop, smartphone, etc.) connecting to a network is a potential entry point for hackers. These devices are typically the first attack vector criminals test when trying to hack into a system. If an endpoint turns out to be vulnerable, the intruder breaks into an otherwise secure network without having to "crack" its primary cyber defenses.
This article is an intro to endpoint security that explains how companies protect what many describe as the weakest link in network security. Read on to learn what it takes to keep would-be hackers out of endpoints and ensure these devices do not become a doorway to your assets and data.

Endpoint protection is a subset of the broader network infrastructure security, an area of cybersecurity that focuses on protecting the network's underlying hardware and software.
What is Endpoint Security?
Endpoint security (or endpoint protection) is the practice of keeping endpoint devices safe from external and insider threats. The primary goals of endpoint security are to:
- Prevent unauthorized access to assets.
- Detect suspicious user behavior.
- Stop in-progress attacks.
- Detect and isolate threats before they do damage to the network.
- Help the team identify and mitigate the root cause(s) of threats.
Any device or system that communicates with the network from outside its firewall is an endpoint. Nowadays, this definition extends far beyond the PCs we use for work — here's a list of all the endpoints modern organizations must secure and account for:
- Laptops.
- Tablets.
- Desktop computers.
- Mobile phones.
- Internet of Things (IoT) gadgets and sensors (thermostats, biometric scanning devices, security cameras, etc.).
- Wearables (i.e., smart watches or medical devices).
- Smart printers.
- Servers (both on and off-site).
- POS devices.
- Industrial machines.
- Network hardware (routers, switches, etc.).
- Virtual machines.
- Operational Technology (OT) systems.
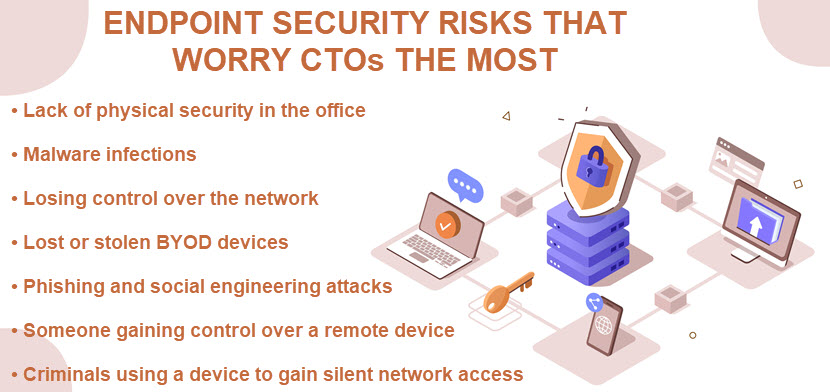
The number of internet-enabled devices is at an all-time high, so companies have their hands full when preparing for attacks. Here are some of the most common endpoint security risks a team is likely to face:
- Lost or stolen devices.
- Phishing attacks (a social engineering strategy that tries to trick the user into sharing sensitive data (such as a password) or clicking on a malware-infected link).
- Ransomware (a type of malware that encrypts the victim's data and asks for money in exchange for the decryption key).
- An endpoint becoming a part of a DDoS bot.
- Malvertising (infected ads that install malware if the user clicks on them).
- Drive-by downloads (hidden software downloads that occur without the user's knowledge).
- Spyware (malware that tracks user activity).
- Installation of unsafe applications.
These risks are only the tip of the iceberg. Check out our article on the different types of cyberattacks to get an in-depth breakdown of the current cybercrime landscape.
Why is Endpoint Security Important?
Any device with access to a network is a potential target for an attack, but some devices are easier to hack than others. For example, a personal phone connected to the office Wi-Fi is significantly less challenging to crack than the main server. While there's less to gain from hacking an endpoint, the phone is still a worthwhile objective as it likely has access to some business data.
Sometimes, going after data accessible to a specific endpoint is not the primary goal of an attack. More skilled hackers know how to compromise an endpoint and then use the device for lateral movement to reach valuable databases or set up an APT threat.
A recent study reveals that almost 70% of successful data breaches originate at an endpoint device. Here are a few other figures that show the criticality of keeping endpoints safe:
- In 2022, almost 68% of organizations have experienced at least one endpoint attack that impacted data or IT infrastructure.
- Over 48% of organizations are unsatisfied with their current level of endpoint security.
- An average organization allows 55% of all endpoints to access some sensitive data.
- One in three U.S. employees uses a personal, non-BYOD device to work remotely.
- The cost of a successful endpoint attack in the US now sits at $8.94 million (this figure was $7.1 million in 2021).
Security concerns aside, high levels of endpoint protection are often a prerequisite for meeting compliance. Many industries and regions require a business to keep endpoints safe to comply with regulations (especially if devices have access to sensitive user data).
Read about the business world's most common (and strictest) regulations and see what it takes to ensure compliance:
- HIPAA Compliance Checklist
- Compliance Guide to GDPR
- PCI Compliance Checklist
- How to Achieve SOC 2 Compliance
You can also check out our CCPA vs. GDPR article for a detailed comparison of the two most prominent data privacy regulations.
What Are the Types of Endpoint Security?
There are three main types of endpoint security: Endpoint Protection Platforms (EPP), Endpoint Detection and Response (EDR), and Extended Detection and Response (XDR).
Endpoint Protection Platform (EPP)
EPPs primarily focus on preventing malware and are comparable to what you'd expect from a reactive antivirus program. These platforms help deal with threats by:
- Comparing files against a database of known attack signatures.
- Using machine learning to detect suspicious activity on an endpoint.
- Enabling the creation of lists that block or allow specific apps, URLs, ports, IP addresses, etc.
- Providing sandboxes to test suspicious executables.
Admins deploy an EPP directly on endpoints, but a central platform continually analyzes data (either on-prem or in the cloud).
Endpoint Detection and Response (EDR)
An EDR offers the same features as EPPs but also has the capability to respond to active threats in real time. These platforms enable an admin to:
- Set up automatic remediation processes (e.g., isolate a dangerous file or wipe the endpoint's memory if something goes wrong).
- Identify indicators of compromise (IoC).
- Get real-time alerts on security incidents.
EDRs detect threats invisible to an EPP, such as file-less malware or polymorphic attacks.
Extended Detection and Response (XDR)
An XDR platform offers better protection and deeper risk analysis than an EDR. XDRs provide more visibility and rely heavily on automation to correlate and eliminate threats.
An XDR tool crosses multiple security layers (endpoints, network traffic, etc.) and consolidates data from:
- Security information and event management (SIEM) tools.
- EPPs and EDRs.
- Network analytics.
- Identity and access management (IAM) tools.
The main goal of XDR is to reduce incident response times, enable more context during threat inspection, and provide in-depth analysis of affected endpoints to identify the root cause of the threat.
How Does Endpoint Protection Work?
Endpoint security relies on a client/server model. A centrally managed server hosts the primary security program (which analyzes threats and makes decisions) and an accompanying client program on each endpoint (which collects data and sends info to the main server).
There are three different strategies based on where you host the primary security program:
- On-premises deployment: In this strategy, the client software runs in an on-site server room.
- Software-as-a-service (SaaS) model: In the SaaS model, a cloud provider hosts and manages the client software.
- Hybrid model: A hybrid approach mixes both on-prem and cloud solutions.
No matter where you run the primary endpoint security software, the protection principles stay the same. Programs on endpoints gather data and send it to the central platform, which checks the files, processes, and systems for suspicious activity. Platforms primarily detect oddities in two ways:
- Checking data packets against a database of known attack signatures (excellent at detecting known threats).
- Performing behavioral analysis to uncover potentially suspicious activity of users or systems (excellent at identifying new hacking tactics and even some zero-day exploits).
If the platform discovers a threat, it instructs the endpoint to block traffic and isolate the file from the network. The security team then investigates the threat (or the platform performs predefined mitigation steps). The endpoint does not reconnect to the network until the team eliminates the risk.
Consider boosting your endpoint security with Managed Detection and Response (MDR), an outsourced service that proactively identifies and removes IT threats (and does so at a significantly lower price than what an in-house security team would set you back).
What's the Difference Between Antivirus and Endpoint Security?
An antivirus is a type of cybersecurity software that detects and isolates malicious files (malware, viruses, worms, Trojans, etc.). Endpoint security, on the other hand, is a broader term that encompasses a wider range of measures for protecting endpoints and their associated networks from threats (including malicious software).
Antivirus programs are a subset of endpoint security. No endpoint security strategy is complete without an antivirus (firewalls are the other bare-bones necessity). Even the most basic EPP will have some form of antivirus protection.
Here are the most notable differences between antivirus and endpoint security:
- Scope: Antivirus software protects one device, whereas endpoint security aims to protect all connected devices across an enterprise network.
- Go-to threats: Antivirus programs only stop malware-based attacks, while endpoint security entails protection from a broader set of dangers (data theft, CEO fraud, SQL injections, etc.).
- Protection strategy: An antivirus protects a device by comparing traffic against a database of known threats. Endpoint security platforms rely on a similar database, but these tools also check for advanced vulnerabilities based on behavioral analysis.
- Updates: Most traditional antiviruses require manual updates. Modern EPPs and EDRs running in the cloud update automatically, taking the burden off the security team and end-users.
- Protection against insider threats: Antiviruses typically offer little to no protection against insider threats (e.g., someone putting sensitive data on a USB drive and stealing valuable files). Endpoint security offers far greater protection from threats like intentional file deletion, unauthorized access, and data leakage.
Continue learning about how companies keep systems safe by checking out our in-depth article on the different types of network security.
Features to Look for in an Endpoint Security Tool
Here is a list of features you should expect to get from a top-tier endpoint security tool:
- An antivirus program that detects and removes threats from endpoint devices.
- A firewall to filter outgoing and incoming traffic on endpoints.
- Intrusion Prevention Systems (IPS) to monitor network traffic for signs of malicious activity and block threats before they do any damage. An IPS is a more advanced version of an Intrusion Detection System (IDS).
- Capability to detect suspicious behavior of users, apps, and network services.
- Automated incident response plans.
- End-to-end data encryption (at rest, in transit, and in use).
- App controls that enable you to create "allowlists" and "blocklists," ensuring users install only approved software on endpoints.
- Mobile device management (MDM) features for managing and securing mobile devices.
- Internet-of-Things security that ensures IoT devices and sensors are free of exploits.
- Continuous monitoring capabilities that ensure you're safe around the clock.
- Device controls that enable you to control which devices can upload or download data.
- Data loss protection features that prevent intentional or unintentional data deletion.
- Protection from threats that spread via email (anti-malware scans for attachments and phishing detection).
- Browser protection that bans certain websites and stops drive-by downloads.
- Anti-exfiltration capabilities that block files transmitted via email, collaboration tools, or the Internet.
- Real-time reporting and alerting that provide prioritized warnings regarding threats.
- Sandboxing features that enable endpoints to test suspicious executables in an isolated environment without access to any sensitive network areas.
- Rollbacks to a previous device state (one of the critical practices in ransomware prevention).
- Threat forensics to help identify the scope and root cause of dangers.
Looking to boost your security levels? Check out our article on the best network security tools on the market and see whether you find a few platforms worth adding to your current tool stack.
Despite Advances, Endpoints Are Still a Go-To Target for Attacks
Modern endpoint security has come a long way from old-school antiviruses and firewalls. Nowadays, platforms provide a broader set of defenses to counter both known and unknown threats. However, despite these advancements, endpoints remain an enticing target for attacks. Organizations must ensure hackers cannot use these devices as an easy-to-crack door into their network.



