Do you feel intimidated by the complexities of HIPAA? Achieving compliance is undoubtedly challenging, considering the many administrative and technical requirements.
Fortunately, our HIPAA checklist is here to help. From developing privacy policies to implementing security safeguards, our checklist covers it all, giving you a structured roadmap to navigate the intricacies of HIPAA and establish a proactive approach to compliance.
Simplify your journey and embark on a path to success with our comprehensive checklist—a powerful tool designed to streamline your efforts.

HIPAA Compliance Checklist
Despite being a federal law, the Health Insurance Portability and Accountability Act (HIPAA) does not have universal compliance standards. Instead, HIPAA’s governing body, The Office for Civil Rights (OCR), individually evaluates organizations based on their risk profiles. They hold higher-risk organizations to a more exacting standard of “reasonable and adequate” measures.
However, they also expect all organizations to handle protected health information (PHI) with the utmost care and impose significant fines and penalties for violations, especially in cases of negligence or malice.
Here are the steps to HIPAA compliance ranked by priority:
1. Appoint a Privacy and Security Officer
The initial step of an effective HIPAA compliance strategy should always be to appoint a privacy and security officer. They will be the central personnel overseeing your organization’s compliance program.
Consider the size and budget of your organization when deciding between hiring a full-time staff member or assigning the responsibilities to qualified compliance or IT staff. In smaller organizations, it may be feasible for one individual to handle both roles.
The designated privacy officer will have the following responsibilities:
- Oversee all aspects of HIPAA compliance.
- Serve as the primary point of contact for patients, employees, and regulatory agencies regarding HIPAA-related matters.
- Organize workforce training and education programs on HIPAA compliance.
- Monitor and assess privacy practices to ensure adherence to HIPAA.
- Develop and implement security measures to protect PHI.
- Schedule regular reviews of policies to ensure they align with current HIPAA guidelines and address any necessary updates.
- Document any breaches or incidents involving protected health information, following appropriate incident response protocols.
2. Establish HIPAA Compliance Policies and Documentation
It is vital to develop comprehensive written privacy and security policies and a code of conduct that applies to all staff. Meticulously documenting HIPAA-related policies enables you to establish a clear framework for compliance and provides you with valuable evidence in case of an audit.
Additionally, regular reviews of your compliance policies and procedures are crucial to staying aligned with evolving requirements, regulatory changes, and emerging best practices. By recording updates and modifications, you demonstrate your commitment to security and establish a traceable history of your efforts.
3. Create PHI Safeguards
To ensure the security of PHI, you must implement appropriate protection measures. These safeguards are classified into three categories: technical, administrative, and physical.
- Technical safeguards center on leveraging technology to ensure the secure transmission and storage of PHI. These measures bolster defenses against cyber-attacks, reinforcing overall protection against data breaches by malicious actors. Examples of technical safeguards include virtual private networks (VPNs), firewalls, and Intrusion Detection Systems.
- Administrative safeguards ensure that only authorized employees who require access to PHI for their job functions are granted permission. For instance, when an employee with access is terminated, the organization must prevent any further access to PHI by that individual.
- Physical safeguards protect PHI from unauthorized access, theft, and damage. Examples of these safeguards include facility access controls, surveillance cameras, environmental controls, perimeter security, and proper disposal of PHI.
Storing PHI in the cloud is a viable option. However, it requires following specific procedures and guidelines. Read our latest article on HIPAA cloud storage requirements to discover how to securely store PHI in the cloud.
4. Conduct Workforce Training
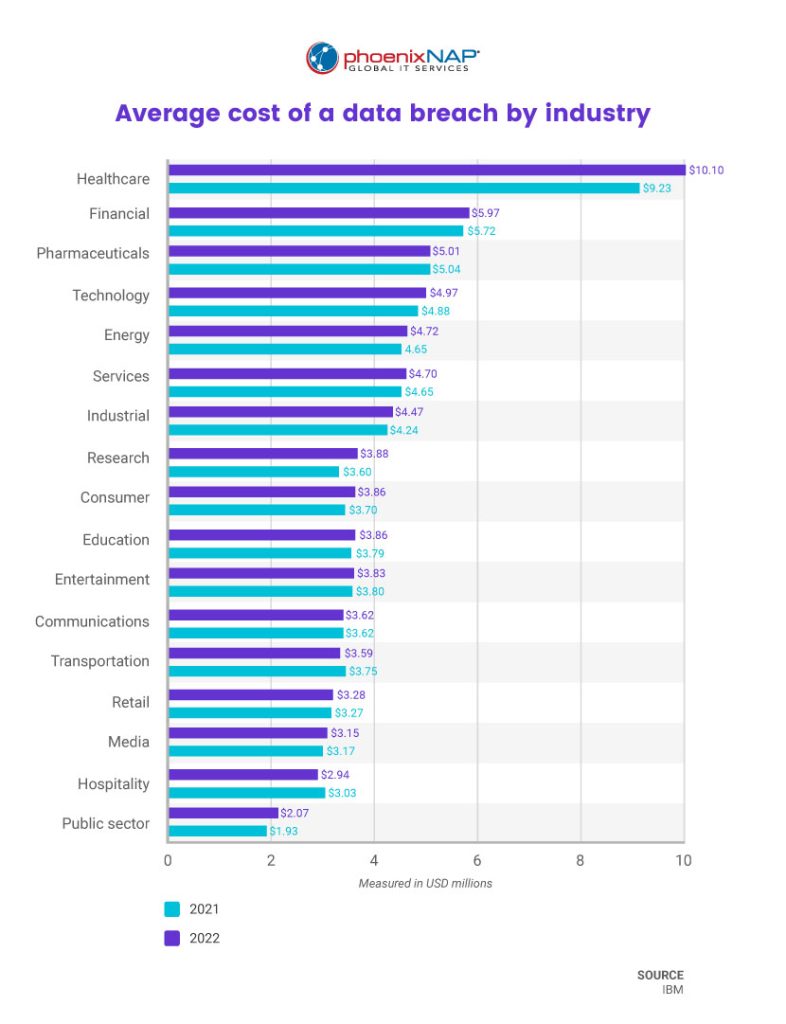
A recent study found that 88% of data breaches are caused by employee error. That is why effective HIPAA compliance relies on a well-trained and vigilant workforce. All individuals handling PHI, including contractors and part-time employees, must know how to effectively secure it during storage, transit, and at rest.
HIPAA training programs should include the following:
- An overview of HIPAA, with a focus on the key provisions of the Privacy and Security Rules.
- Essential skills in recognizing and preventing common types of cyber-attacks, such as phishing, social engineering, and ransomware.
- The best practices for securing PHI, particularly physical and workstation security, and proper data backup and data storage procedures.
- Education on email security best practices and encryption protocols for secure communication.
Providing HIPAA training to new hires shortly after their start date is fundamental, and annual retraining is mandatory to maintain compliance. Additionally, you need to document completed training sessions, as auditors often request access to training records spanning 3-4 years.
5. Conduct a Thorough Risk Assessment
In the aftermath of a breach, one of the primary documents the OCR will want to see is your risk assessment – a systematic evaluation of potential vulnerability to unauthorized PHI access.
By identifying and documenting known risks and installing mitigation measures, your risk assessment serves as tangible evidence that any potential data breach was an unforeseen risk rather than intentional disregard of HIPAA rules.
Beyond its role in satisfying audit requirements, a proactive approach to risk management identifies gaps before they evolve into significant issues and reduces the likelihood of the OCR exposing unaddressed vulnerabilities during an audit.
6. Sign and Review Business Associate Agreements
Protecting PHI goes beyond internal efforts; it extends to your business associates (BAs). As a covered entity, it is your responsibility to ensure that BAs adhere to HIPAA. However, the OCR also holds BAs legally accountable for their compliance, highlighting the interdependent relationship between covered entities and business associates.
Here are three examples of HIPAA business associates:
- IT Service Provider. A small medical practice may engage an IT service provider to manage their computer systems, network infrastructure, and data storage. Since the IT service provider has access to PHI while maintaining and supporting the practice’s technology, they fall under the business associate category.
- Medical Transcription Company. If the medical practice outsources transcribing patient records or dictations, the medical transcription company becomes a business associate. They handle and process PHI on behalf of the practice, making them responsible for complying with HIPAA.
- Billing and Coding Service. Many small medical practices outsource their billing and coding tasks to specialized service providers. These companies handle patient billing information, treatment codes, and other sensitive data related to healthcare reimbursement, making them business associates under HIPAA.
To establish a solid foundation for compliance, it is essential to sign Business Associate Agreements (BAAs) with all relevant partners who handle PHI. These agreements serve as legal documents that define the obligations and responsibilities of both parties and ensure that your BAs understand their role in maintaining compliance and protecting PHI. Furthermore, you must conduct regular reviews and updates of all business associate agreements. As HIPAA requirements evolve, it is crucial for BAAs to accurately reflect the current regulatory landscape.
One of the requirements of HIPAA-compliant Gmail is signing a Business Associate Agreement with Google. Click the link to find out more.
7. Create a Robust Backup Strategy
Timely access to medical records is a fundamental right under HIPAA. Healthcare organizations must fulfill patient requests within 30 days or face fines of up to $4.3 million for “willful neglect.”
To ensure compliance with HIPAA’s retrieval and delivery requirements for medical records, organizations must establish a strong data backup strategy as a key component of compliance. This strategy is essential for information recovery in scenarios such as accidental deletion, system failures, cyber-attacks, or natural disasters.
Organizations should also regularly test their backup and disaster recovery plans to ensure they function as intended and that they can accurately restore data when needed. Testing also identifies potential weaknesses in the strategy, strengthening the organization’s overall data protection and HIPAA compliance.
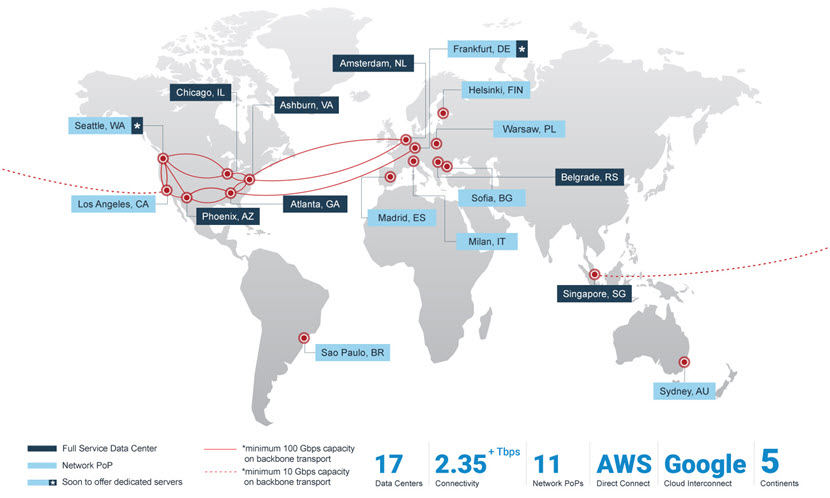
Having servers in multiple regions enhances redundancy and reduces the risk of data loss. In the event of a local server failure or disaster in one region, our global network of HIPAA-ready servers can be quickly restored from backups in other locations.
8. Create a Breach Notification Procedure
According to the Breach Notification Rule of HIPAA, if your organization suffers a security incident that exposes PHI, you must submit a breach report to the OCR within 60 days of discovering it. You must also notify the affected individuals within the same period, as well as the local media, if the breach impacted more than 500 people.
It is essential to outline a clear and well-defined plan that delineates all the necessary steps in case of a breach. Here are the key components of a breach notification plan:
- Identify and Define a Breach. Clearly define what constitutes a breach according to HIPAA and determine the criteria that trigger the breach notification procedure.
- Establish a Response Team. Create an internal response team for managing incidents. This team should include representatives from legal, IT, compliance, and senior management to ensure a coordinated and swift response.
- Create an Incident Assessment Protocol. Create a procedure for gathering all necessary information about the nature and scope of a PHI security incident. Evaluate the potential risk of harm to those affected, considering factors like the type and amount of PHI involved.
- Notification Determination. Based on the assessment protocol, create a system for determining whether breach notification is required.
- Notification Process. Develop a clear process for notifying affected individuals, including the OCR and local media outlets.
- Documentation and Recordkeeping. Maintain detailed documentation of all breaches, including incident assessments, notification records, and any actions to address the damage.
It is important to note that BAs are not exempt from the breach notification rule and are legally obligated to report any incidents involving PHI to the appropriate parties, just like covered entities.
Who Needs to Comply With HIPAA?
All organizations and individuals that handle protected health information (PHI) must comply with HIPAA’s Security, Privacy, and Breach notification rules. PHI is any identifiable health information related to an individual’s past, present, or future physical or mental health.
Three types of organizations have distinct requirements under HIPAA:
- Covered entities include hospitals, doctors, pharmacies, and health insurance companies. They are directly involved in creating and transmitting PHI and must adhere to the full scope of HIPAA.
- Business associates like consultants, accounting firms, IT providers, and lawyers. They handle PHI acquired from covered entities but are not involved in its creation and subsequently have less responsibility under HIPAA.
- Subcontractors such as cloud hosting providers and shredding companies. They are hired by business associates for niche roles and may have access to PHI, making HIPAA applicable to them as well.

Download the HIPAA Compliance Checklist
Don’t let compliance challenges overwhelm you—take a proactive approach. Download our HIPAA Compliance Checklist PDF and streamline your compliance efforts.
A HIPAA compliance checklist outlines the key requirements and measures for organizations to achieve HIPAA compliance. It is a step-by-step guide that addresses all the essential components of HIPAA compliance, including administrative, physical, and technical requirements.
By using a HIPAA compliance checklist, organizations can systematically review and implement the necessary measures to meet HIPAA’s stringent privacy and security standards, helping to protect sensitive patient information and mitigate potential risks.
Why Do You Need a HIPAA Compliance Checklist?
Completing a HIPAA checklist demonstrates your diligence in ensuring a secure environment for PHI. A completed checklist is, therefore, compelling and valuable evidence during a HIPAA audit.
The Office for Civil Rights (OCR), the primary enforcement authority of HIPAA, employs audits as the main control mechanism. They are typically triggered by public exposure of a HIPAA violation via the media, whistleblowers, or disgruntled patients. The OCR typically only conducts random audits for larger, more prominent companies or as part of a Corrective Action Plan for previous offenders.
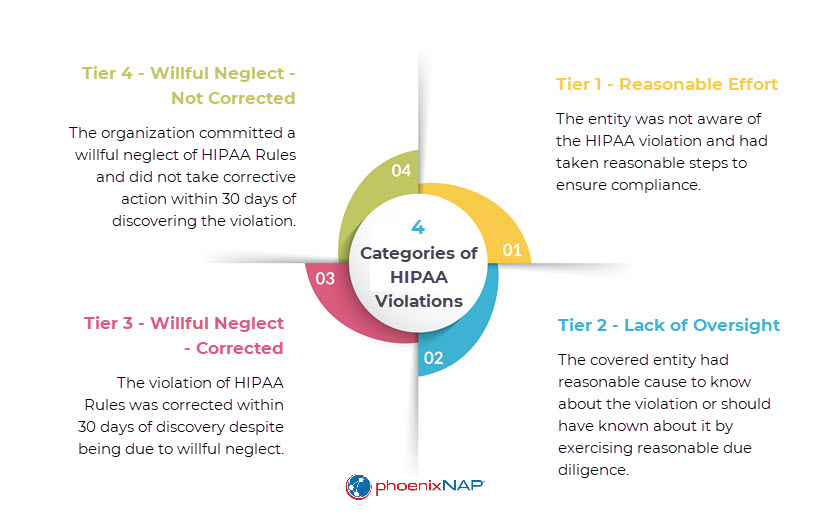
Violating HIPAA can have devastating consequences. HIPAA violations in the workplace commonly end with the firing of the offending employee or a loss of medical licensure and accreditation. Intentional or reckless violations can result in fines and penalties, class action lawsuits, and up to 10 years in prison. If a HIPAA violation receives media attention, the offender’s reputation and income are often severely damaged as they lose public trust.
Conclusion
Despite the potentially intimidating nature of HIPAA, the OCR’s standards aren’t unrealistically high. You can be compliant with a relatively modest investment in infrastructure, staff, and training. Furthermore, when it comes to unintentional violations, the OCR generally adopts a forgiving approach. In most instances, their initial course of action is to offer technical support and advice for improving compliance.
Investing resources into cybersecurity also pays for itself. A robust cyber security infrastructure minimizes the potential impact of devastating cyber-attacks, to which the healthcare sector is particularly susceptible. Investing in cyber security also contributes to the seamless functioning of day-to-day operations.
Ultimately, HIPAA compliance should be pursued for its own sake because it protects the confidentiality of medical information and builds public trust in medical institutions. When patients know that their sensitive medical information is handled with care and protected from unauthorized access, they will be more confident in seeking healthcare services and sharing necessary details.



