Identifying and eliminating vulnerabilities in systems and applications is a priority in cybersecurity. Organizations use various techniques to uncover software flaws, but penetration testing is the most realistic and comprehensive method for analyzing security weaknesses. By simulating real-world cyberattacks, penetration testing assesses the effectiveness of security measures and exposes vulnerabilities that might otherwise remain undetected. Understanding how penetration testing works and how organizations leverage these tests to prevent costly and damaging breaches is essential for strengthening cybersecurity defenses.
This article provides an in-depth introduction to penetration testing, its methodologies, stages, tools, and its vital role in protecting digital assets.

What Is Penetration Testing?
Penetration testing is a systematic attempt to evaluate the security of an IT infrastructure by safely exploiting vulnerabilities. These vulnerabilities may exist in operating systems, services, applications, improper configurations, or risky end-user behavior. The primary goal of penetration testing is to identify security weaknesses before malicious actors can exploit them, thereby preventing data breaches, financial losses, and damage to an organization's reputation.
Penetration testers, often called ethical hackers, use the same tools, techniques, and processes as attackers to find and demonstrate the business impacts of weaknesses in a system. By simulating real-world attacks, penetration testing provides a realistic assessment of an organization's security posture, enabling stakeholders to prioritize remediation efforts effectively.
Types of Penetration Testing
Penetration testing is classified into various types based on the scope, objectives, and the amount of information shared with the testers.
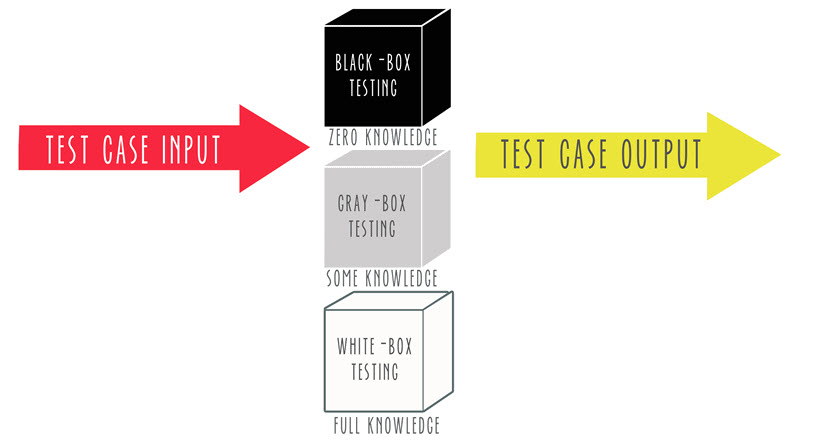
Black Box Penetration Testing
In black box penetration testing, the tester has no prior knowledge of the target system's internal workings. The tester approaches the assessment as an uninformed cybercriminal would, relying solely on publicly available information and the tester's skills to identify vulnerabilities.
This method provides a realistic simulation of external threats but requires more time due to the extensive reconnaissance involved.
White Box Penetration Testing
White box penetration testing provides the tester with comprehensive information about the target system, including network diagrams, source code, credentials, and architecture details.
This approach allows for an in-depth examination of the security posture, focusing on internal vulnerabilities such as insecure coding practices and system misconfigurations. White box testing is efficient and thorough but may not accurately represent an external attacker's perspective.
Read our in-depth comparison of white and black box testing, the two most common setups for a penetration test.
Grey Box Penetration Testing
Grey box penetration testing is a hybrid approach where the tester has partial knowledge of the target system. This knowledge could include limited access credentials or partial architectural information. Grey box testing aims to simulate an attack by an insider or a hacker who has gained unauthorized access to an organization's network.
This method balances the depth of white box testing with the realism of black box testing.
External Penetration Testing
External penetration testing evaluates the security of an organization's external-facing assets, such as web applications, websites, email servers, and network infrastructure accessible from the Internet. The objective is to identify vulnerabilities external attackers could exploit to gain unauthorized access to internal systems and data.
Internal Penetration Testing
Internal penetration testing simulates an attack from within the organization's network. This type of testing assesses the potential impact of an insider threat, such as a disgruntled employee or an attacker who has breached the external defenses and gained access to internal systems. Internal testing evaluates the effectiveness of internal security controls and policies.
Targeted Testing
Targeted testing involves collaboration between the organization's IT team and penetration testers. Both parties know about the testing activities, allowing for real-time feedback and adjustments. This approach is often used to test specific aspects of the security infrastructure or to train the internal security team.
Blind Testing
In blind testing, the penetration tester is provided with limited information, typically only the organization's name. The security team is aware that a test is occurring but does not have details about the tester's methodologies. Blind testing evaluates the organization's security monitoring and incident response capabilities.
Double-Blind Testing
Double-blind testing extends the blind testing approach by keeping both the penetration tester and the security team unaware of specific details. Only a few individuals within the organization are aware of the test. This method provides the most realistic simulation of a real-world attack, assessing both detection and response mechanisms without prior knowledge.
Penetration Testing Methodologies
Organizations typically rely on one of the five main standardized penetration testing methods:
OWASP (Open Web Application Security Project)
The OWASP Testing Guide is a widely recognized framework focusing on web application security. It outlines techniques for identifying and mitigating common vulnerabilities such as:
- SQL injections. Exploiting input fields to execute unauthorized SQL commands.
- Cross-site scripting (XSS). Injecting malicious scripts into web pages viewed by users.
- Insecure direct object references (IDOR). Accessing unauthorized resources by manipulating parameters.
- Security misconfigurations. Identifying weaknesses due to improper configurations.
OWASP provides tools like OWASP ZAP and resources such as the OWASP Top Ten to assist in improving software security through a community-driven approach.
OSSTMM (Open-Source Security Testing Methodology Manual)
OSSTMM offers a scientific and methodological approach to security testing, emphasizing quantitative metrics to measure operational security. It provides guidelines for testing various domains, including information systems, telecommunications, physical security, and social engineering.
Key features of OSSTMM include:
- Quantitative metrics. Objective measurements for trust and risk assessment, aiming for repeatable and verifiable results.
- Rules of engagement. Clear guidelines defining the scope and limitations of testing activities.
- Comprehensive coverage. Addressing multiple security channels to provide a holistic assessment.
ISSAF (Information System Security Assessment Framework)
ISSAF is a broad framework for assessing information system security. It is particularly useful for complex environments that require meticulous documentation. The framework covers both technical aspects (e.g., network security, application security) and non-technical aspects (e.g., policies, procedures, and organizational culture), ensuring a holistic evaluation of the security posture.
ISSAF also encourages using a variety of tools and methods to ensure thoroughness, including both automated and manual testing techniques.
PTES (Penetration Testing Execution Standard)
PTES defines a standard for penetration testing by outlining seven main sections to promote consistency and comprehensiveness:
- Pre-engagement interactions. Establishing scope, goals, and legal considerations.
- Intelligence gathering. Collecting information about the target organization.
- Threat modeling. Identifying potential threats and vulnerabilities.
- Vulnerability analysis. Scanning and analyzing systems for weaknesses.
- Exploitation. Attempting to exploit identified vulnerabilities.
- Post-exploitation. Assessing the impact and extent of access gained.
- Reporting. Documenting findings and providing remediation recommendations.
NIST (National Institute of Standards and Technology)
NIST provides cybersecurity guidelines and best practices through its Special Publications. In particular, NIST SP 800-115 offers a technical guide to information security testing and assessment, covering comprehensive procedures for planning, execution, analysis, and reporting.
This framework is popular within high-danger industries like banking, communications, and energy. Compliance with NIST standards is often required for U.S. federal agencies, organizations handling government data, and American businesses in general.
Each standardized methodology offers a unique approach to penetration testing:
• OWASP focuses on web application security with techniques for common vulnerabilities.
• OSSTMM emphasizes a quantitative, scientific approach across multiple security domains for repeatable results.
• ISSAF provides detailed processes suitable for complex environments needing meticulous documentation.
• PTES ensures consistency by outlining all phases of the penetration testing process.
• NIST offers guidelines aligned with regulatory compliance, especially for government-related organizations.
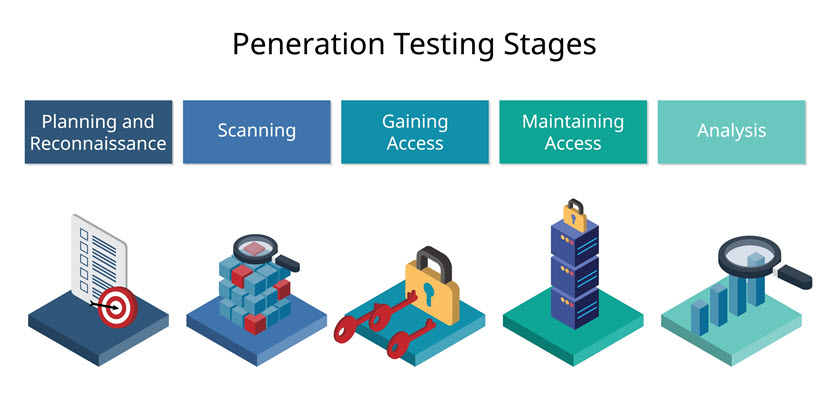
What Are the Stages of Penetration Testing?
Penetration testing follows a structured process consisting of the following stages:
Planning and Reconnaissance
The planning and reconnaissance stage involves the initial preparation and information gathering required to conduct a successful penetration test. This phase sets the foundation by establishing clear objectives and collecting essential data about the target systems.
Defining Scope and Objectives
In this phase, the penetration tester collaborates with the organization to define the scope, objectives, and rules of engagement for the test. Clear communication ensures that both parties understand what will be tested and the desired outcomes. Key activities include:
- Establishing goals. Identifying what the organization aims to achieve, such as uncovering vulnerabilities, testing incident response capabilities, or meeting compliance requirements.
- Setting scope. Determining the specific systems, networks, applications, and assets to be tested, ensuring all critical areas are included.
- Agreeing on rules. Outlining the testing boundaries, permissible techniques, and legal considerations to ensure that all activities are authorized and conducted safely.
Information Gathering
After defining the scope and objectives, the tester begins collecting as much information as possible about the target environment. This information is crucial for identifying potential attack vectors and planning effective testing strategies. Activities include:
- Open-source intelligence (OSINT). Gathering data from publicly available sources such as websites, social media profiles, domain registrations, and public records to understand the organization's external footprint.
- Network scanning. Using tools like Nmap to identify live hosts, open ports, and running services, which helps map the network and identify potential entry points.
- Footprinting. Mapping the organization's network architecture, including domain names, IP address ranges, and infrastructure details, to gain a comprehensive view of the target environment.
Scanning and Enumeration
The scanning and enumeration stage involves a deeper analysis of the target systems to identify vulnerabilities and gather detailed information that could be exploited. Scanning and enumeration involve these activities:
- Vulnerability scanning. In this phase, testers use automated tools to detect known vulnerabilities in operating systems, applications, and network devices. This process identifies weaknesses such as missing patches, outdated software, or exploitable misconfigurations.
- Service enumeration. Testers identify services running on open ports and analyze their configurations. Understanding which services are active and how they are set up allows testers to pinpoint potential vulnerabilities associated with specific applications or protocols.
- Banner grabbing. By collecting information from service banners, testers determine software versions and other details that may reveal known vulnerabilities. Banner grabbing helps build an inventory of systems and applications to focus on during exploitation.
Understanding the difference between vulnerability scanning and penetration testing will enable you to create a comprehensive security testing strategy.
Exploitation
The exploitation phase involves actively attempting to breach the security of the target systems by exploiting identified vulnerabilities. This stage demonstrates the potential impact of a successful attack. During the exploitation phase, testers perform the following actions:
- Attack execution. Testers use exploit tools and scripts to bypass security controls and gain unauthorized access to systems, applications, or data.
- Privilege escalation. After initial access, testers attempt to increase their level of access to obtain higher privileges, allowing them to control more critical parts of the system.
- Lateral movement. Testers navigate through the network to access additional systems and sensitive information, simulating how an attacker might expand their foothold within the environment.
Post-Exploitation
Following successful exploitation, testers assess the extent of their access and the potential impact on the organization. This stage helps in understanding the risks associated with a security breach. Key activities during this stage include:
- Data exfiltration simulation. Demonstrating the ability to extract sensitive data, such as customer information, intellectual property, or financial records.
- Persistence techniques. Establishing methods to maintain access over time, such as installing backdoors or creating unauthorized user accounts.
- Impact analysis. Evaluating the potential damage in terms of data loss, operational disruption, financial costs, and reputational harm to the organization.
Reporting
Comprehensive reporting is essential to communicate the penetration test findings to stakeholders effectively. The report provides a detailed account of vulnerabilities discovered and recommendations for remediation. Key components of the reporting phase include:
- Detailed documentation. Providing a thorough description of testing activities, including methodologies, tools used, and step-by-step accounts of how vulnerabilities were exploited.
- Risk assessment. Categorizing vulnerabilities based on their severity, likelihood of exploitation, and potential impact on the organization.
- Recommendations. Offering actionable guidance for addressing each identified vulnerability, including technical solutions and suggestions for improving security policies and procedures.
Remediation and Retesting
After receiving the penetration test report, the organization addresses the identified vulnerabilities. Remediation and retesting ensure that security weaknesses are effectively mitigated. This stage involves:
- Implementing fixes. Taking corrective actions such as applying patches, updating software, reconfiguring systems, or enhancing security controls.
- Verification testing. Retesting the systems to confirm that the vulnerabilities have been successfully addressed and no new issues have been introduced.
- Continuous improvement. Incorporating lessons learned into the organization's security strategy, updating policies, and planning for future security assessments to maintain a strong security posture.
Penetration Testing Tools
Below is a list of essential tools commonly used in penetration testing:
- Nmap (Network Mapper). A tool for network discovery and security auditing; used to scan networks and identify open ports and services.
- Metasploit Framework. An open-source platform for developing and executing exploit code against target systems.
- Wireshark. A network protocol analyzer that captures and displays packets in real time, useful for network troubleshooting and analysis.
- Burp Suite. An integrated platform for performing web application security testing, including intercepting proxy, scanner, and intruder tools.
- John the Ripper. A fast password cracker that supports various encryption technologies, used to detect weak passwords.
- Nikto. A web server scanner that tests for dangerous files, outdated versions, and server misconfigurations.
- SQLmap. An automated tool for detecting and exploiting SQL injection vulnerabilities in web applications.
- Aircrack-ng. A suite of tools for assessing Wi-Fi network security, including monitoring, attacking, testing, and cracking.
- Hydra. A parallelized network login cracker supporting numerous protocols; used for brute-force password attacks.
- OWASP ZAP (Zed Attack Proxy). A tool designed to find vulnerabilities in web applications; particularly useful for beginners.
- Nessus. A comprehensive vulnerability scanner that identifies vulnerabilities in operating systems, applications, and devices.
- Maltego. An open-source intelligence and forensics application that provides data mining and link analysis.
- Kali Linux. A Linux distribution designed for penetration testing and digital forensics; preloaded with numerous security tools.
- Canary Tokens. A system for detecting unauthorized activities through the use of decoy tokens.
- Social Engineering Toolkit (SET). A framework for simulating social engineering attacks, including phishing campaigns.
Read our article on the best penetration testing tools for an in-depth exploration of the latest security software on the market.

Advantages and Disadvantages of Penetration Testing
You must understand both the benefits and limitations of penetration testing to make informed decisions about its implementation.
Advantages of Penetration Testing
Penetration testing offers the following benefits:
- Simulates real-world attacks. Penetration testing models real-world attacks, demonstrating how actual threats would impact the organization. For example, a tester might discover a flaw in a web application that allows unauthorized access to confidential customer data, highlighting a critical issue that needs immediate attention.
- Uncovers complex security flaws. Penetration testing uncovers complex security flaws that automated tools might miss. For instance, a penetration tester might find that combining two minor vulnerabilities enables them to bypass authentication entirely, revealing a serious security gap.
Disadvantages of Penetration Testing
Penetration testing presents the following challenges and risks:
- Limited scope. Penetration tests often focus on specific areas, potentially missing vulnerabilities outside the defined scope. For example, concentrating only on network security might lead to overlooking weaknesses in web applications or mobile platforms.
- Time-consuming and costly. Penetration testing is time-intensive and requires skilled professionals and extensive resources, making it more expensive than automated methods like vulnerability scanning.
- Risk of system disruption. If mishandled, penetration testing causes outages or data loss. For example, testing certain exploits can crash a server, interrupting business continuity if you do not have a backup.
Penetration Testing FAQ
Below are answers to frequently asked questions about penetration testing.
Who Performs Penetration Testing?
Penetration testing is conducted by skilled professionals known as penetration testers or ethical hackers. These individuals possess in-depth knowledge of cybersecurity principles, attack methodologies, and defensive strategies. They are proficient in various programming languages, networking concepts, and security tools.
Penetration testers often hold industry-recognized certifications, such as:
- Certified Ethical Hacker (CEH).
- Offensive Security Certified Professional (OSCP).
- Certified Information Systems Security Professional (CISSP).
- GIAC Penetration Tester (GPEN).
- CompTIA PenTest+.
Organizations may employ in-house penetration testers or engage external security firms specializing in penetration testing services.
Can I Do My Own Penetration Testing?
While organizations can perform basic security assessments internally, conducting comprehensive penetration testing requires specialized skills and experience. Attempting to perform penetration testing without proper expertise often leads to incomplete assessments or unintended consequences, such as system disruptions, downtime, or legal issues.
Employing professional penetration testers ensures that the testing is thorough, legally compliant, and aligned with cybersecurity best practices. External testers also provide an objective evaluation and may identify vulnerabilities that internal teams might overlook due to familiarity or bias.
When To Perform Penetration Testing?
You should conduct penetration testing proactively to identify and address vulnerabilities before attackers exploit them. Key scenarios when penetration testing is essential include:
- Before a system goes live. Testing new systems, applications, or networks before deployment ensures that vulnerabilities are identified and remediated early.
- After significant changes. Performing tests following major updates, upgrades, or configuration changes to systems and infrastructure verifies that security controls remain effective.
- In response to emerging threats. Testing strengthens defenses against new attack techniques or vulnerabilities that have been disclosed publicly.
- To meet compliance requirements. Regular penetration testing is mandated by industry regulations such as PCI DSS, HIPAA, or GDPR.
- Following a security incident. Conducting tests after a breach or attempted attack helps assess the extent of vulnerabilities and prevent future incidents.
How Often Do You Perform Penetration Testing?
The frequency of penetration testing depends on factors such as the organization's size, industry, regulatory obligations, and risk tolerance. General recommendations include:
- Annually. At a minimum, organizations should perform comprehensive penetration testing once a year.
- Biannually or quarterly. High-risk environments like those managing sensitive financial or personal data require more frequent testing.
- After significant changes. Conduct tests whenever there are substantial modifications to the infrastructure, applications, or security policies.
- Continuous testing. Implementing ongoing security assessments and vulnerability scanning to maintain an up-to-date understanding of the security posture.
Does Penetration Testing Require Coding?
Penetration testing frequently demands proficiency in coding and scripting languages, enabling testers to develop custom exploits by creating or modifying code to target specific vulnerabilities. Coding skills are also essential for automating repetitive tasks, such as scanning and data collection, making the testing process more efficient. Additionally, penetration testers analyze source code to identify security flaws within applications, while understanding application behavior allows them to interpret software functions and uncover logical vulnerabilities.
Proficiency in languages such as Python, Ruby, Perl, JavaScript, or C/C++ enhances a tester's ability to conduct comprehensive assessments.
Is Penetration Testing Legal?
Penetration testing is legal only when conducted with explicit authorization from system owners, with legal considerations including written consent that outlines the scope and limitations of testing activities. Testers must also comply with local, national, and international data protection regulations to ensure adherence to legal standards. Additionally, ethical conduct is paramount, as testers are expected to follow professional codes of conduct, avoiding unauthorized access or harm to systems and data beyond the agreed-upon scope.
Unauthorized penetration testing, or hacking without consent, is illegal and results in criminal charges and civil lawsuits.
What Happens After Penetration Testing?
After a penetration test, organizations must take the following steps:
- Review the penetration test report. The first step is to review the report provided by the testers. This report outlines the discovered vulnerabilities and offers specific recommendations for remediation.
- Prioritize vulnerabilities. This should be performed based on the severity and likelihood of exploitation. The process involves assigning responsibilities to specific team members, setting clear deadlines for each remediation task, and allocating the necessary resources to address the identified issues.
- Implement security enhancements. This may include applying software patches, updating system configurations, strengthening Identity and Access Management (IAM), and improving network segmentation to limit the impact of potential breaches.
- Update policies and procedures. Organizations must also update their IT security policies and procedures based on the insights gained from the test. Implementing security awareness training helps prevent future vulnerabilities.
- Retest and monitor continuously. Retesting is vital to verify that the vulnerabilities have been effectively resolved. Continuous monitoring and regular security assessments help maintain a strong security posture and adapt to evolving threats.
How Much Does Penetration Testing Cost?
The cost of penetration testing varies based on the following factors:
- Scope and complexity. Larger networks and complex systems require more time and effort to assess.
- Depth of testing. Comprehensive tests that include social engineering, physical security, and in-depth code analysis are more expensive.
- Expertise of testers. Highly qualified and experienced testers charge higher fees.
- Type of testing. Specialized tests, such as wireless or cloud penetration testing incur additional costs.
- Geographic location. Costs vary widely based on regional market rates and the availability of qualified professionals.
On average, penetration testing services range from $4,000 to over $100,000. Small businesses might spend around $4,000 to $20,000, while larger companies could incur costs exceeding $50,000 for extensive assessments.

Read our article on IT cost reduction to learn how to optimize your IT budget without causing turmoil.
Strengthening Cybersecurity with Penetration Testing
Penetration testing is a vital component of strengthening an organization's cybersecurity defenses. Simulating real-world attacks uncovers hidden vulnerabilities that malicious actors could exploit. Despite its limitations, such as higher costs and the potential for system disruptions, the insights gained from penetration testing are precious.
In an era of increasingly sophisticated and common cyber attacks, penetration testing is essential for any organization committed to maintaining strong cybersecurity.



