No matter how much an organization invests in cybersecurity, it's impossible to avoid ransomware attacks. The sheer number of attack attempts (approx. 236 million globally in the first half of 2022 alone) means some malicious programs will eventually slip past defenses and enter your system.
Once ransomware is inside the network, your goal is to detect and isolate the threat before it encrypts too much data. This article presents the most effective ransomware detection techniques for identifying malicious software as early into the infection process as possible.
Check out our overview of famous ransomware examples to learn different strategies criminals use to infect systems.
What are Ransomware Detection Techniques?
Ransomware detection techniques are various methods and strategies IT security teams use to identify signs of ransomware presence in networks. The goal of these techniques is to detect malicious software before it makes lateral moves and starts encrypting data (i.e., as early in the cyber kill chain as possible).
Detecting signs of ransomware before it does any damage to data is challenging. Recent studies show that around 73% of successful ransomware infections encrypt at least some data. Here are a few other stats that demonstrate how quickly ransomware operates once inside a system:
- Over 97% of ransomware attacks require less than 4 hours to complete their objective (i.e., encrypt all files with a certain extension or in a specific system directory).
- An average ransomware script requires around 45 minutes to encrypt 100,000 files.
- Some advanced ransomware variants infiltrate and assume system control in less than 45 seconds. Many of these "premium" programs are available via subscription-based ransomware-as-a-service.
Here are other factors that make ransomware detection challenging:
- Criminals use a variety of avenues to inject ransomware into a system (e.g., infected executables in emails or SMS messages, phishing, fake online ads, insider threats, etc.)
- Some ransomware uses advanced techniques to evade detection, such as encrypting its code or changing signatures.
- Hackers often rely on zero-day attacks to exploit unknown vulnerabilities in programs and operating systems.
- In some cases, ransomware does not require the installation or execution of a file on the target system (traditionally a tell-tale sign of malware setup).
- Criminals know how to hide ransomware within legitimate software to escape detection. The go-to options in recent years are PowerShell scripts, VBScript, and PsExec.
Security experts predict that there will be a new ransomware attack every two seconds by 2031. Not even top-tier detection can keep up with that pace, making proactive ransomware prevention as vital as identifying signs of infection.
The Urgency of Early Detection
The earlier you detect signs of any type of cyberattack, the better your odds of preventing damage and limiting the blast radius. This rule is especially true for ransomware as the consequences of this attack are often severe and irreversible.
The longer it takes for a company to detect ransomware, the more time malicious programs have to:
- Encrypt data.
- Exfiltrate files.
- Set up back doors for future attacks.
- Spread across the network and reach other machines and databases.
Early ransomware detection is especially vital for companies without up-to-date data backups. If malicious software encrypts data you haven't backup up, the only way to restore files is to pay the ransom (and there's no guarantee you'll get the decryption key even if you meet the criminal's demands).
In 2022, the average ransom payment was $812,360. However, the average cost of recovering fully from a successful attack was $4.5 million, a figure that accounts for the full expenses of:
- Paying the ransom.
- Recovering lost data.
- Restoring IT systems to pre-incident state.
- Paying legal fines for allowing data breaches and leakages.
- Losing customers (both old and new) due to reputation hits.
- Being unable to maintain operations without access to the necessary data.
Ready to reinforce your anti-ransomware tool kit? Boost both your detection and prevention capabilities with PhoenixNAP's ransomware protection and our unique mix of immutable backups, cloud-based disaster recovery, and cutting-edge infrastructure security.
Common Ransomware Signs
The signs of ransomware presence vary based on the specific type of program that entered the network, but there are a few universal indicators of infection. Here are the most common signs of scripts searching for and encrypting files:
- Missing or inaccessible files or folders.
- New files with strange extensions.
- Unusual spikes in disk activity.
- Slow computer or network performance.
- Disabled or cleared system event logs.
- Strange changes to security settings.
- The creation of new privileged accounts.
- Disabled or missing anti-malware and virus tools.
- Suspicious login activities.
- Applications crashing, not opening, or becoming unresponsive.
- Suspicious inbound and outbound network traffic (often a sign of a ransomware script communicating with a Command and Control (C&C) server).
- Presence of unauthorized software (such as Microsoft Process Explorer, MimiKatz, IOBit Uninstaller, or PC Hunter).
- Deleted system backups and recovery partitions.
- Unauthorized network scans (a common sign of someone trying to move laterally between systems).
Ensure your team has a go-to incident response plan in case they identify signs of ransomware in your network.
Best Ransomware Detection Techniques
Modern ransomware scripts easily bypass basic security measures, so teams must rely on more advanced strategies. There are three primary ransomware detection techniques:
- Signature-based detection, which identifies binary signatures of malicious programs.
- Behavioral detection, which evaluates the behavior of users, programs, and OS processes.
- Deception-based techniques, which attempt to trick malicious software into executing in a safe environment.
Using multiple techniques at once improves your chances of detecting ransomware programs before they do damage. Know the pros and cons of each strategy, but don't hesitate to use all three detection techniques to protect your systems and data.
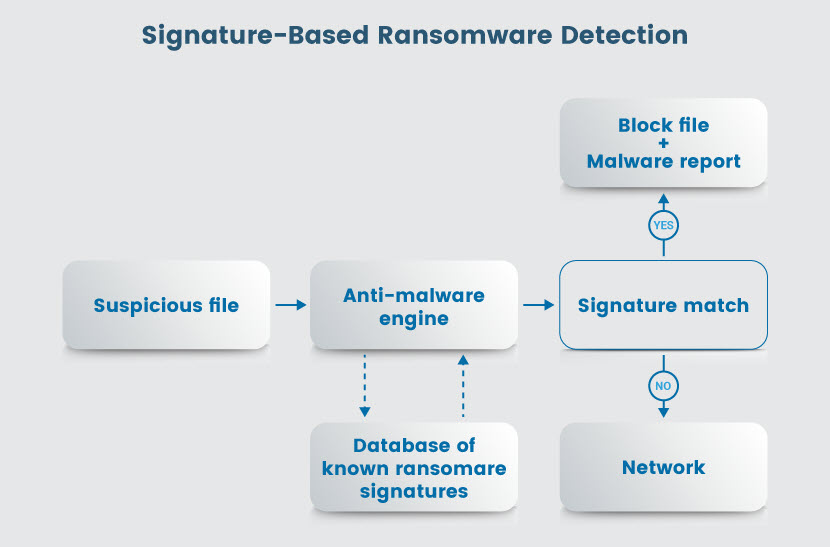
Signature-Based Ransomware Detection
Signature-based detection platforms compare the digital signature of a file or program against a database of known ransomware binary hashes. Signatures include data that uniquely identify a specific malware variant.
Whenever a new file enters or runs on a system, the tool compares it against the library of previously found signatures to determine the likelihood of ransomware presence. The tool flags all suspicious files without running the code, either quarantining or deleting the file (depending on settings) before alerting the security team.
Pros of signature-based ransomware detection:
- Excellent at recognizing well-known ransomware samples and strains.
- Low false positive rate.
- Does not impact device performance or cause network latency.
- Identifies malicious files before execution, preventing the program from encrypting any data.
Cons of signature-based ransomware detection:
- Unable to recognize new malware variants since these have unknown signatures.
- Even a slight change in file hashes decreases the malicious software's detectability.
- Often struggles with encrypted ransomware files.
- No protection against customized, targeted attacks that use unique versions of malware.
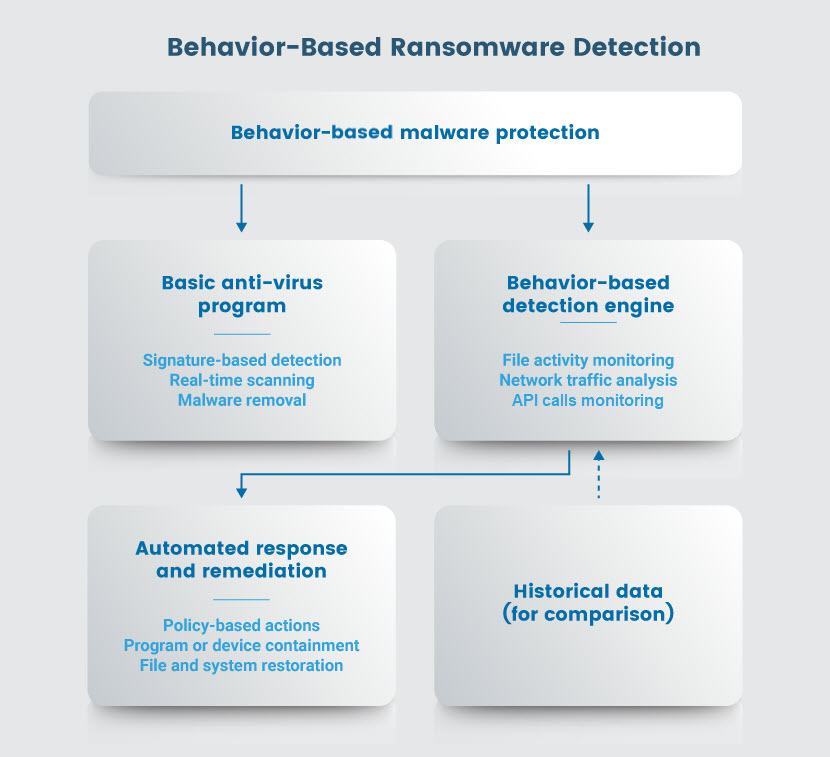
Behavior-Based Ransomware Detection
Behavior-based detection focuses on identifying patterns of behavior that are:
- Typical of ransomware attacks.
- Atypical of usual network activity.
Compared to signature-based solutions, behavior-based detection does not require "knowing" a signature. Here are a few examples of what these tools would flag:
- An employee accessing a company desktop remotely from another state.
- A program attempting to modify a large number of files at once.
- Software encrypting files with an unusual extension.
- Someone making too many changes to system settings.
- A process causing sudden outbound traffic spikes in the middle of the night.
There are three distinct behavior-based detection methods:
- File system changes: This method inspects abnormal file processes (e.g., too many file renames in a short time frame, suspicious extensions, or new copies with greater entropy than original files).
- Traffic analysis: This method detects traffic anomalies at the network level (e.g., software connecting to a shady file-sharing site or sudden spikes in data transfer volumes).
- API calls: This method examines unusual API calls (e.g., suspicious commands or commands executed in an unusual volume or context).
Pros of behavior-based ransomware detection:
- Takes advantage of the fact all ransomware causes unusual system behavior.
- Reliably detects novel and modified ransomware scripts.
- Excellent at stopping hackers and malicious programs from exfiltrating data.
Cons of behavior-based ransomware detection:
- Yields a high number of false positives, all of which require individual inspection.
- Often blocks legitimate operations, resulting in downtime and hurting productivity.
- Analyzing behavior takes more time than checking a signature, so scripts often manage to encrypt some data before alerting the platform.
- Vulnerable if attackers use legitimate file-sharing sites or IP addresses.
- More skilled hackers know how to bypass behavior-based detection by adding delays between encryptions or by spawning multiple processes to encrypt file groups.
- Often leads to high CPU utilization on endpoints.
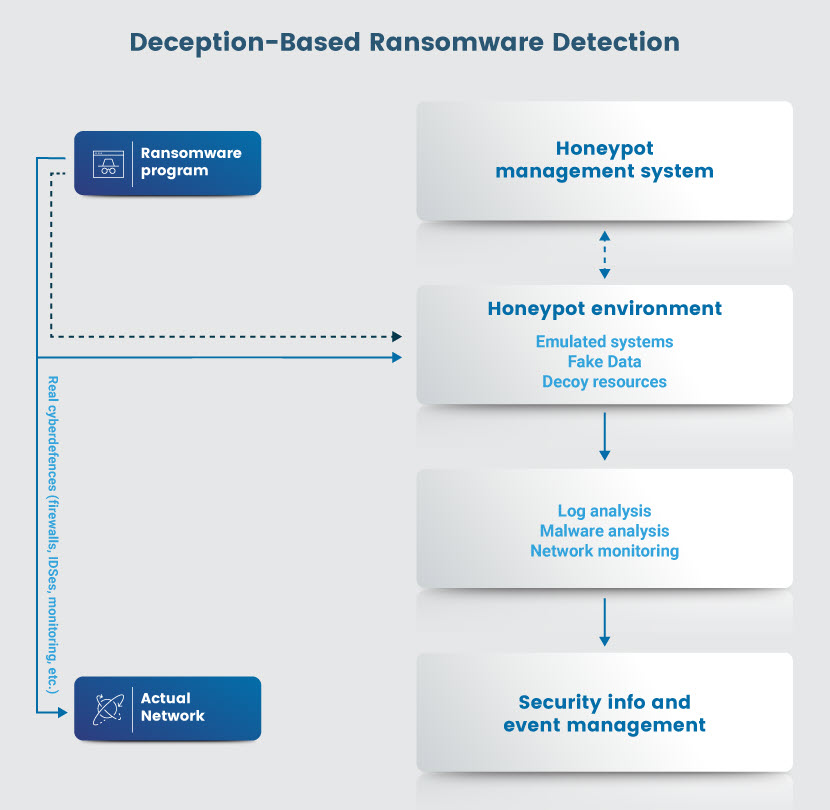
Deception-Based Ransomware Detection
Deception-based detection tricks malicious programs into activating in controlled environments where there's no real business data. The main idea is to create decoys (fake files and systems) that look like worthwhile targets for attacks.
These repositories or servers (typically referred to as honeypots) are full of fake files the security team places in a visible location in the network to act as bait. No app or employee uses these servers, so any activity in the honeypot is a clear indicator of a network intrusion.
Once a honeypot activates, the security team contains the threat, analyzes its nature, and ensures the same malicious program does not reach anything of value.
Pros of deception-based ransomware detection:
- Detects ransomware that signature and behavior-based platforms miss.
- Excellent at detecting new ransomware variants.
- Reveals the attacker's techniques, tools, and procedures (TTPs) in a safe setting, helping security teams boost the protection of real databases.
Cons of deception-based ransomware detection:
- Takes time to set up and maintain.
- Making a honeypot appear as a legitimate database or server is challenging.
- Occasionally leads to false positives as programs and users may interact with the bait files by accident.
Ransomware Detection Best Practices
Here are a few best practices that further improve your chances of identifying ransomware presence:
- Improve network monitoring: Enhance network monitoring capabilities to gain better visibility of east-west traffic activity and more reliably detect unauthorized attempts at lateral movement.
- Use an IDS tool: Intrusion detection systems are excellent at identifying attempts to communicate with systems via a C&C server. Common activities an IDS reliably detects include sending commands, storing keys, exfiltrating data, and monitoring system responses.
- Train the team to recognize signs of ransomware: Organize regular security awareness training to educate employees on the threat of ransomware. Ensure everyone knows how to recognize signs of infection and what to do if they notice anything suspicious.
- Use threshold alerting: Threshold alerting enables a system to respond to events that match or exceed a pre-defined threshold. For example, if a program encrypts an X number of files within a given period, a script could stop the process, change firewall settings, or isolate a specific endpoint.
- Segment your network: Use network segmentation to isolate critical systems and improve the chances of detecting intrusions.
- Keep systems up to date: The team must apply the latest patches to systems and apps as soon as updates become available. Regular patching improves the odds of detecting the latest ransomware variants that exploit freshly discovered vulnerabilities.
- Boost endpoint security: Most malware originates on employee devices, and ransomware is no exception. High levels of endpoint security significantly boost your ability to detect and isolate threats before they spread to other devices.
As an extra precaution, consider investing in managed detection and response (MDR). This third-party service provides access to highly trained teams with tons of experience in identifying and eliminating malware-based threats.
Don't Overlook the Value of Early Ransomware Detection
Reliable ransomware detection ensures the few intruders who manage to breach your network do little to no permanent damage. Without that security layer, you risk cybercriminals having free reign to do whatever they want once they slip past defenses (which, judging by recent statistics, is bound to happen sooner or later).
This is why it's of utmost importance to have a ransomware recovery plan ready for when the time comes. Learn how to recover from a ransomware attack with minimal downtime and data loss.