Introduction
SSH port forwarding and SSH tunneling are two interchangeable terms. An encrypted SSH tunnel transfers assorted data and delivers it safely to the remote system. This method is used to circumvent standard firewall security protocols. Port forwarding is a component of most SSH client and server programs.
This article explains SSH port forwarding and shows how to use OpenSSH for Linux and the Windows PuTTY client to enable local, remote, or dynamic SSH port forwarding.
Prerequisites
- An SSH client/server of your choice (OpenSSH or PuTTY).
- A reachable IP address or name of the remote/local server.
What Is SSH Port Forwarding (SSH Tunneling)?
SSH port forwarding, also known as SSH tunneling, securely transports data over an encrypted SSH connection. It works by forwarding connections from a local port on your machine through an encrypted tunnel to a remote machine. This technique allows users to securely access services that are otherwise restricted by network policies.
In practice, SSH port forwarding allows you to access network resources that are not directly reachable. For instance, if you are offsite and need to connect to a protected resource within a secure network, you can establish an SSH connection to an accessible machine within that network. This SSH connection then serves as a tunnel that forwards your requests to the protected resource.
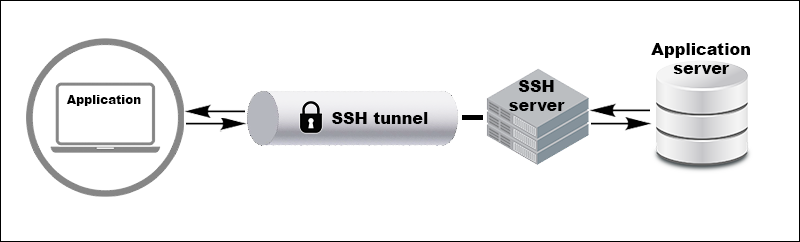
What Is an SSH Tunnel?
An SSH tunnel is a secure, encrypted pathway between your local machine and a remote server over an SSH connection. This tunnel is a secure way to transfer data and protect sensitive information from eavesdropping or interception.
You can securely forward network traffic from a local port to a specified destination using an SSH tunnel. This is useful for accessing restricted services or resources that are otherwise unreachable due to firewall or network configurations.
Types of Port Forwarding
There are several types of port forwarding, each designed to meet specific needs. The main types include:
- Local port forwarding.
- Remote port forwarding.
- Dynamic port forwarding.
The sections below explain each type in detail.
Local Port Forwarding
Local port forwarding redirects traffic from your local machine to another server through an intermediary, often using an SSH tunnel. For example, if you are at a coffee shop and need to securely access your company's internal database, you can set up local port forwarding.
Local port forwarding creates a secure connection from your machine to the database, making it seem like you are accessing it from your company's network.
Remote Port Forwarding
Remote port forwarding routes traffic from a remote server back to your local machine or another specified destination. This method enables external access to services running on your local machine via an SSH tunnel.
For instance, you can use remote port forwarding if you are developing an app on your machine and want to share it with a client without deploying it to a public server. This allows the client to access the app on your machine securely.
Dynamic Port Forwarding
Dynamic port forwarding sets up a secure, adaptable tunnel for routing traffic from various ports, often through a SOCKS proxy, to different destinations based on real-time needs. It acts as a secure line and channels your internet traffic through your home or office network for added security.
This type of port forwarding is useful when you need to securely access multiple resources, like email or work databases, while traveling and using public Wi-Fi.
How Does SSH Port Forwarding Work?
SSH port forwarding creates a secure tunnel between a local and a remote machine. This allows data to travel securely over an encrypted SSH connection. Once the SSH tunnel is established, the SSH client listens on a specified local port. It then forwards any traffic arriving at that port through the connection to the corresponding remote port.
This process makes the remote service accessible as if running on a local machine without exposing it to the internet. The SSH client and server manage data encryption and decryption to keep all transmitted information confidential.
Network traffic is directed to a specific port on the target computer. When that computer has an open port, it can receive data on that port. To avoid exposing your computer to the internet with open ports, your router acts as the primary defense against various probes and attacks.
Port forwarding allows legitimate traffic to pass through to your network by specifying rules on the router, such as the IP address and port. This directs data packets to the correct machine waiting for an SSH connection, ensuring secure access to remote services.
Benefits of SSH Port Forwarding
SSH port forwarding is a popular method for securely accessing remote services and networks. The key benefits of SSH port forwarding are:
- Enhanced security. Utilizes strong SSH keys and encryption to authenticate users and protect data, preventing unauthorized access and eavesdropping.
- Data confidentiality. Encrypts data in transit and ensures that sensitive information is secure and inaccessible to potential attackers.
- Access control. Allows secure access to remote services and networks without exposing them directly to the internet.
- Bypassing of network restrictions. Enables users to bypass firewalls and network restrictions by tunneling through an encrypted SSH connection.
- Ease of use. Simple command-line syntax and user-friendly programs make setting up and managing SSH tunnels straightforward for beginners and experienced users.
Disadvantages of SSH Port Forwarding
While SSH port forwarding provides significant security benefits, it also comes with some drawbacks:
- Performance bottlenecks. Since all data is routed through the SSH tunnel, it can slow down network performance and potentially create congestion.
- Complex management. Managing multiple SSH tunnels can be complex, especially in environments with many ports or services requiring forwarding.
- Security risks. Improperly configured or unsecured tunnels can expose systems to unauthorized access and potential data breaches.
- Single point of failure. If the SSH server or connection fails, all forwarded services through that tunnel become inaccessible.
- Resource intensive. Maintaining encrypted tunnels consumes hardware resources, which can impact system performance.
How to Set up Local Port Forwarding
Critical network resources do not generally allow remote SSH access, which is a severe limitation in a modern distributed environment. Organizations usually solve this issue by setting up an intermediary SSH 'jump' server to accept remote SSH connections.
Your local SSH client establishes a connection with the remote SSH server. The connection is then forwarded to a resource within the trusted internal network. SSH connections are established, and security efforts can concentrate on the intermediary SSH server rather than individual resources in a network.
Local Port Forwarding with OpenSSH
To use SSH tunneling in Linux, you must provide your client with the source and destination port numbers, as well as the location of the destination server. The location can either be an IP address or a hostname.
The basic syntax for a local port forward is:
ssh -L local_port:destination_server_ip:remote_port ssh_server_hostnamessh- Starts the SSH client program on the local machine and establishes a secure connection to the remote SSH server.-L local_port:destination_server_ip:remote_port- The local port on the local client is being forwarded to the port of the destination remote server. Replace with your values.ssh_server_hostname- This syntax element represents the hostname or IP address of the remote SSH server.
A practical example of an SSH port forwarding command is:
ssh -L 5901:188.17.0.5:4492 [email protected]In the example above, all traffic sent to port 5901 on your local host is being forwarded to port 4492 on the remote server located at 188.17.0.5.
Local Port Forwarding with PuTTY
PuTTY is a user-friendly SSH client for Windows. Configure local SSH tunneling by following these steps when you start the PuTTY application:
1. Enter the hostname or IP address and port number of the destination SSH server in the Sessions screen. For example, [email protected] and port number 22.
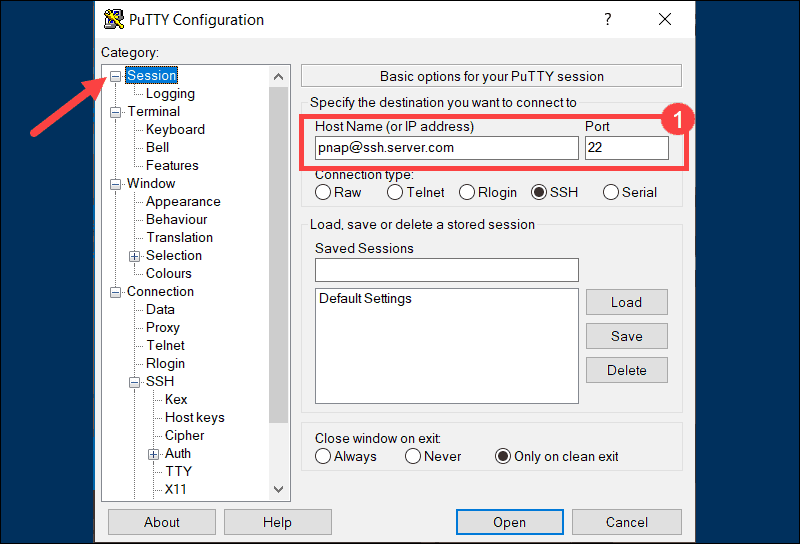
2. Use the Category list on the left to navigate to Connection > SSH > Tunnels.
3. Select Local to define the type of SSH port forward.
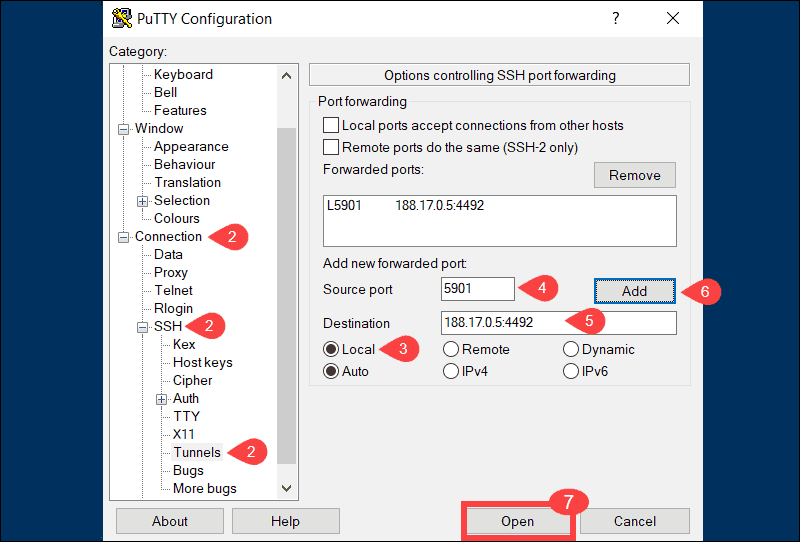
4. Enter your local port number in the Source port field.
5. Type the destination address and port number in the Destination field. Use the following format:
destination_server_ip:remote_portFor example, Source port: 5901, Destination: 188.17.0.5:4492.
6. Once you verify that the information you entered is correct, select Add.
7. The parameters for the connection are now all set. The Open option initiates the local SSH port-forward.
Note: If you are an Ubuntu user, refer to our tutorial How to Install PuTTY on Ubuntu.
How to Set up Remote Port Forwarding
The purpose of remote forwarding is to allow a remote server to access resources on your local machine. Remote forwarding represents an inversion of the local forwarding process.
Remote Port Forwarding with OpenSSH
The basic syntax for a remote port forward command is as follows:
ssh -R remote_port:localhost:local_port ssh_server_hostnameIn the following example, we instruct the remote server ssh.server.com to forward any connections directed at port 8080 to the local resource listening on port 5534:
ssh –R 8080:localhost:5534 [email protected]Users with access to the SSH server are now able to access resources on the local machine.
Remote Port Forwarding with PuTTY
Start the PuTTY application and follow these steps:
1. Specify the IP address and port number of the destination SSH server in the Sessions screen.

2. Use the Category list on the left to navigate to Connection > SSH > Tunnels.
3. Select Remote to define the type of SSH port forward.
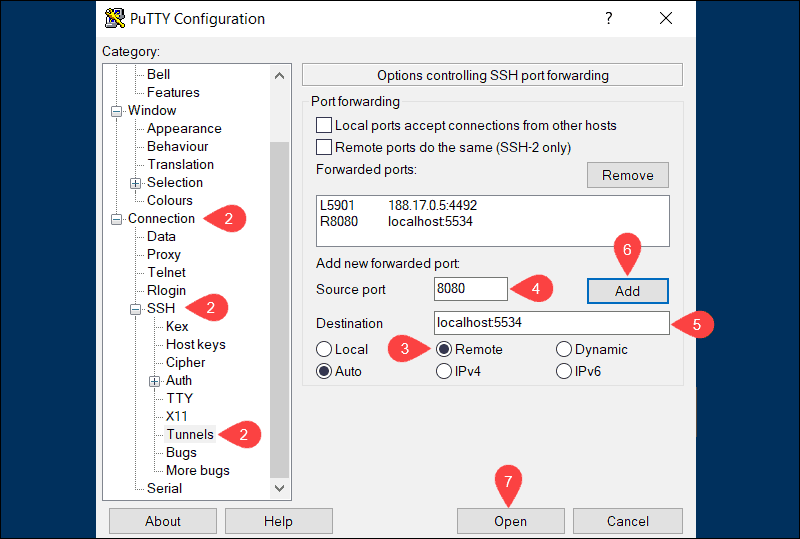
4. Enter the remote port number in the Source port field (e.g., 8080).
5. Type the destination address and port number in the Destination field using the following format:
localhost:local_portFor example:
<code>localhost:55346. Once you verify that the information you entered is correct, click Add.
7. Select Open to establish a remote SSH port-forward.
In the example above, users and applications can connect to port 8080 on the remote SSH server and then access the local machine using port 5534.
Note: Learn how to forward ports with iptables in Linux.
How To Set up Dynamic Port Forwarding
Dynamic port forwarding is less well-known than the previous two options. Most users find it easier to use local port forwarding to achieve similar results. However, dynamic port forwarding can provide more flexibility, as you no longer need to use a predefined remote port and server.
Note: When using dynamic port forwarding, it’s necessary to configure individual programs to use the SOCKS proxy server.
Dynamic Port Forwarding with OpenSSH
By using the ssh command and the -D argument, you can use your SSH client to create a SOCKS proxy on your local machine. The syntax is:
ssh -D local_port ssh_server_hostnameFor example, the following command opens a SOCKS proxy at port 5534 on your local machine:
ssh -D 5534 [email protected]You now can configure a local resource, like a browser, to use port 5534. All traffic originating from that resource is directed through the SSH connections established for the defined port.
Dynamic Port Forwarding with PuTTY
Follow the steps below to set up dynamic port forwarding with PuTTY on Windows:
1. Enter the hostname or IP address and port number of the destination SSH server on the main PuTTY Sessions screen.

2. Use the Category list to navigate to Connection > SSH > Tunnels.
3. Select Dynamic to define the type of SSH port forward.
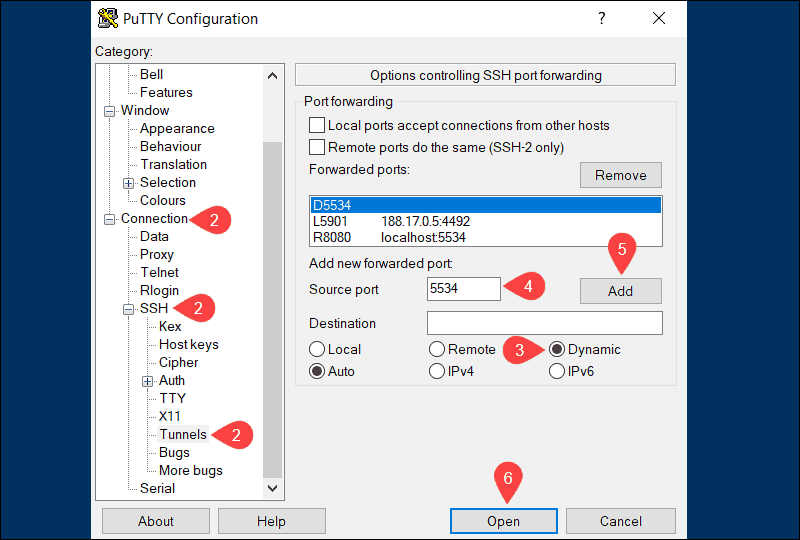
4. Enter the dynamic port number in the Source port field (e.g., 5534). The SOCKS proxy server on your local machine will use this port to dynamically forward traffic.
5. Once you are sure that the information you entered is correct, click Add.
6. The parameters for the connection are now all set. Click Open to start dynamic SSH port-forwarding.
For dynamic forwarding to work, configure and enable each application for the SOCKS proxy server.
Note: If you are working with Kubernetes, you might find our guide about kubectl port-forward useful.
Troubleshooting SSH Port Forwarding Issues
You may encounter some issues when setting up SSH forwarding. This section explores the most common issues and provides possible solutions.
Empty Response
If you are trying to set up remote port forwarding and get an empty response message as the one below:
ERR_EMPTY_RESPONSEThe solution is to use 127.0.0.1 instead of localhost. Port forwarding does not work well on ipv6 in Windows, and using 127.0.0.1 forces it to use ipv4 instead.
Note: Find out the differences between ipv4 and ipv6.
Connection Refused
If communication between your local machine and remote server breaks down, you might get an SSH Connection refused error. There are multiple possible causes of this error, including wrong credentials, incorrect firewall settings, or a closed SSH port.
Read our tutorial on how to fix the SSH connection refused error to find the solution for the causes mentioned above and more.
Port Already in Use
If you are trying to bind a local port, which is already in use by another application, the program throws the following error:
bind: Address already in useThe solution is to choose a different local port for forwarding or to check which process is using the port with the following syntax:
lsof -ti:port_numberAfter you find which application is using the port, you can kill that process to free the port for SSH port forwarding. However, be careful when terminating the process, as it can solve immediate issues but might lead to other problems, especially if the process is critical.
Conclusion
This tutorial explained how SSH port forwarding works and presented three different types of SSH port forwarding with the commands you need to use. SSH port forwarding is a powerful feature that must be carefully administered. High-security standards should be maintained throughout the entire process.
Next, learn to generate SSH keys in Windows or Ubuntu.