Weak and easy-to-guess passwords make even the soundest cybersecurity strategy easy to bypass. If a hacker guesses or cracks a password, the intruder can access your account or system without raising the alarm and compromise whatever asset you kept safe behind a password.
The guide below provides 11 strong password ideas that will help you stay a step ahead of hackers. We also explain the difference between sound and weak passphrases, provide tips on improving current passwords, and show the main methods hackers rely on to crack credentials.

How to Create a Strong Password (with Examples)
A strong password is a unique word or phrase a hacker cannot easily guess or crack. Here are the main traits of a reliable, secure password:
- At least 12 characters long (the longer, the better).
- Has a combination of upper and lowercase letters, numbers, punctuation, and special symbols.
- Random and unique.
While complexity improves password security, length is the key characteristic. The best way to make a password strong is to make it long. For example, look at these two passwords:
- 89&^598
- ILoveMyCatLordStewart
While 89&^598 is entirely random, the first password is less secure than the second one. A password-cracking program could guess the 89&^598 in about 44 hours while cracking ILoveMyCatLordStewart would require 7 years of constant processing.
However, even the 7-years mark is not enough to call a password safe, which is why all strong password ideas below lead to phrases that take significantly longer to crack.
Note: Use phoenixNAP password generator tool to securely generate strong and complex passwords .
The 4 Random Words Method
One of the simplest yet most effective strong password ideas is to throw 4 or more seemingly random words together. Just make sure that:
- The password is at least 12 characters long.
- The words do not have any natural flow to them (such as My Name Is Steven).
- You separate words with either spaces, punctuation, or special symbols.
Some examples of these passwords (and how to remember them) include:
- Phoenix Drive Cafe Office ("I work in Phoenix and drive by a cafe every day on my way to the office").
- Seattle, Kindle, Coffee, Planes ("Seattle is the birthplace of Amazon, Starbucks, and Boeing").
- Minnesota Airplane Boston Christmas ("I live in Minnesota but fly back home to Boston every Christmas").
The time needed to crack the Phoenix Drive Cafe Office password: 2 million years
Use an Entire Phrase
If you do not want to remember a random sequence of words, you can make a password out of a custom phase. Words within a phrase flow together better than random words and are easier to remember, but you should not rely on a famous saying or a quote.
You can decide whether to include spaces between the words (if the website accepts spaces within passwords). Here are a few good examples of custom phrases:
- You can actually use spaces in your password!
- Myboysareinthehighschoolbasketballteam
- I would prefer to go to Gryffindor pls
The time needed to crack the You can actually use spaces in your password! password: 4 hundred trillion years
Use a Custom Acronym
You can use an acronym to create a memorable yet effective password. For example, you can choose the phrase "My son was born at a Liverpool hospital in 2002" and take the first letter of each word (Mswb@aLhi2002) to create a solid and easy-to-remember password.
If you choose this method, ensure you are not basing the password on a common expression (such as Tb,on2b,titq). Here are some good ideas:
- IoaBMW,wa5782p. ("I own a BMW, with a 5782 plate.").
- H!Mnpintd2r! ("Hey! My new password is not that difficult to remember!").
- 2015wtyIbm1h. ("2015 was the year I bought my first house.").
The time needed to crack the IoaBMW,wa5782p. password: 42 million years
Use the Keyboard Layout
Using the keyboard layout to create a custom pattern is another strong password idea. For example, you can remember something simple as a name (e.g., Jane Austen) and then use the keys above and to the right of the letters (Iwj4 W8e64j). Some good examples are:
- P05r 0t 6u4 %9jye ("Lord of the Rings").
- Y5wjr F4j65wp ^45k9jwp ("Grand Central Terminal").
- J43 &05o F4j65wp _w5o ("New York Central Park").
The time needed to crack the P05r 0t 6u4 %9jye password: 698 million trillion years
Make a Simple Formula
You can make up a custom formula to create a reliable password. For example, you can take any phrase and replace every letter with the next one in the alphabet:
- Cucumbers are tasty! -> Dvdvncfst bsf ubtuz! (time needed to crack: 762 billion trillion years)
You can also take the first letter of every word from the chorus of your favorite song:
- Mamma Mia chorus -> MmhIgammhcIrymmdisammjhmimy (time needed to crack: 129 million trillion years)
These examples may seem like gibberish, but that is exactly what you want to achieve.
Vowel Switching
Take any phrase and replace one vowel with another (for example, A with E). As always, have at least 12 characters and use a random phrase for max protection:
- "Every Monday, I wish it was Friday 🙁 " -> Every Mondey, I wish it wes Fridey : (
- "I like a pub with an all-night open-bar policy" -> I like e pub with en ell-night open-ber policy
- "I hammer nails, but nails hammer the board" -> I hemmer neils, but neils hemmer the boerd
The time needed to crack the Every Mondey, I wish it wes Fridey : ( password: 307 million trillion years

Shorten Each Word
Pick a memorable phrase and remove the first three letters of every word (do not worry if the process deletes the entire word):
- "Workdays are for work, but weekends are for football!" -> kdays k, kends tball!
- "Thursdays are great, but Fridays are better" -> rsdays at, days tter
- "Basketball is my favorite sport after hockey" -> ketball orite rt er key
The time needed to crack the kdays k, kends tball! password: 184 billion years
The Sentence Method (Bruce Schneier Method)
Think of a random sentence and transform it into a password by taking the first two letters of every word. For example:
- "I wish I had more time to think of better passwords…" -> IwiIhamotitothofbepa…
- "Driving by a McDonalds and not stopping takes a lot of willpower" -> DrbyaMcDoannosttaaloofwi
- "Creating a strong password is not that hard after all" -> Crastpaisnothhaafal
The time needed to crack the IwiIhamotitothofbepa... password: 1 billion years
Mix the ISO Codes of Favorite Countries
This fun yet strong password idea requires you to list the ISO codes of your favorite countries or counties you visited (that way, you can update your password every time you visit a new nation). You will get something like this:
- "Canada, Mexico, France, Germany, Japan" -> can mex fra deu jpn
The time needed to crack the "can mex fra deu jpn" password: 424 trillion years
The Math Method
You can use mathematical symbols and equations to create a strong password. These passwords are typically long and full of different symbols, making them an ideal passphrase choice. Some examples are:
- MyDog+MyCat=8legs
- 830-630=TwoHundred
- Children+Xmas=Presents
The time needed to crack the MyDog+MyCat=8legs password: 9 million years
Use a Deliberate Misspelling
You can intentionally misspell words to create unique and secure passwords such as:
- SuperrmenHatseCryptoss
- KryingTeers2Nite
- ILovDoubluMcBurgurs
The time needed to crack the SuperrmenHatseCryptos password: 119 million years
If you decide to use this method, be careful not to use common misspellings (such as "acommodate"). Hackers feed cracking programs with password lists with all usual wording errors, so the more obscure your password is, the better.
Safe passwords are just the beginning of a sound security strategy. Learn what else you need to account for by referring to our article on the most common cybersecurity attack types.
How to Improve an Existing Password
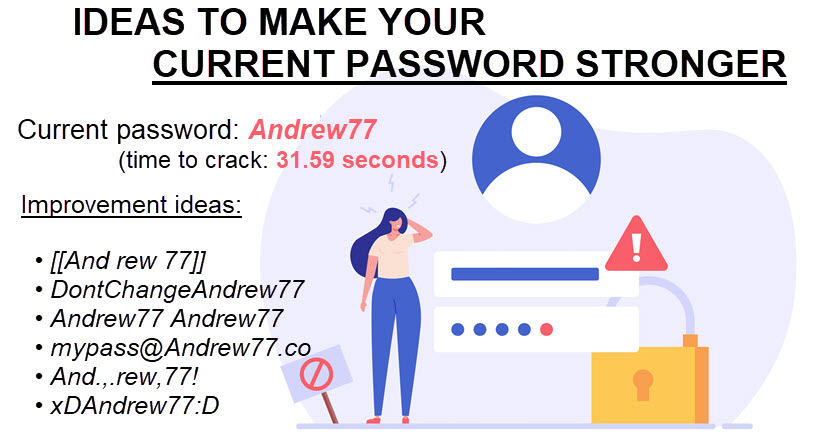
If you have a favorite password you already find easy to remember, you do not have to substitute it with a new passphrase. Instead, you can improve the current weak password by:
- Adding spaces or brackets.
- Adding additional words.
- Repeating the password twice.
- Turning the passphrase into an email address.
- Adding random punctuation.
- Adding emoticons.
- Swapping letters around (if the current password has enough characters to be secure).
Slight changes to a password are also helpful when creating unique passphrases for several accounts. Rather than creating a new password from scratch, you can add a different code to your existing password for each online account (e.g. {Andrew,77}EBAY for your eBay profile and {Andrew,77}PPAL for the PayPal account).
What to Avoid when Choosing a Password
You should follow a strict set of rules when choosing passwords to avoid weaknesses a hacker can exploit. A strong password should never:
- Have less than 12 characters.
- Be solely based on personal data (name, surname, family member's name, date of birth, workplace, favorite sports club, etc.).
- Contain memorable keyboard paths (most notably qwerty and asdfgh).
- Solely use letters, symbols, or numbers.
- Be re-used across two (or more) different accounts or websites (even if the password is strong, one of the websites keeping the password might have a breach and place all other accounts in danger).
- Include sequential letters or numbers.
- Be based on a common word (in any language).
- Rely on basic character substitution for security (such as M@nch3st3rUtd or L3tM31n).
- Contain the corresponding username.
Examples of poor passphrases that may look like strong password ideas are:
- 5404464785: This password has no letters or special characters, plus it uses a phone number.
- March101977: This password uses personal info (someone's birthday), has a common dictionary word (March), and lacks special characters.
- P@ssword12345: While it does have 13 characters, a symbol, numbers, a mix of letters, and no personally identifiable info, a computer can crack this password in 0.01 seconds. P@ssword is a common phrase, and the 12345 sequence is a simple find for any program.
It is also wise to stay clear of any passwords other people widely use. Hackers always start the cracking process by trying the most popular passphrases, such as:
- 111111
- 123123
- 12345678
- jesus
- letmein
- password1
- asdf
- qwerty
- trustno1
- abc123
- dragon
- football
- iloveyou
You can use the Have I Been Pwned? website to test how unique your password is and ensure your passphrase was not a part of any prior data breach.
Additional Security Options to Secure Your Passwords
Besides strong password ideas, you can also rely on other security practices to ensure a password remains safe. The suggestions below are helpful both for securing personal credentials and protecting passwords on a company-wide level.
Multi-Factor Authentication (MFA)
Even if someone steals your password, you can still prevent the intruder from accessing your account. Multi-factor authentication (MFA) adds an extra layer of security to your account by requiring the user to provide the following during login:
- A username and password.
- A biometrics scan or a physical token.
This two or three-step verification process makes it difficult for cybercriminals to gain access and steal your identity.
If you wish to protect your business from stolen identities and passwords, you can implement MFA via a specialized app your employees install on their smartphones. Google's Authenticator and Authy are two great free options, both tools that generate a one-time PIN that serves as an additional factor during login.
Refer to our cybersecurity best practices article for more ideas and advice on protecting your business from cyber threats and check out our Biometrics vs Passwords article to learn about the differences between these two security options.
Virtual Private Networks (VPNs)
You (and your employees) should always use a VPN when typing in or exchanging passwords on public Wi-Fi. A VPN ensures no one is intercepting your username and password when you log into your account.
Besides various other benefits, our Bare Metal Cloud offering also enables you to quickly and easily set up a remote access VPN.
General Password Protection Best Practices
Even the world's toughest password becomes pointless if you do not know how to use and protect it. Be careful with your passphrase by following these best practices:
- Never share your password with anybody.
- If you store passwords online, ensure the website does not store credentials in plaintext.
- Do not save your passwords in an online document, email, or note.
- When choosing security questions in case of a forgotten password, select hard-to-guess options to which only you know the answer. Do not use a question whose answer is easy to find online or on your social media.
- Change passwords regularly, at least once every few months.
- Do not write down your password and store it near your workstation.
- Do not keep the passphrase inside your phone (either as a note or picture).
You should also not allow browsers to save your password. While convenient, this feature means that a single data leak instantly compromises all your accounts.
Password Managers
A password manager keeps track of all your passwords and does the remembering for you. All you remember is the master password which grants access to the management program (which is, hopefully, a strong password protected with MFA).
Password managers keep passphrases safe with encryption. If someone successfully hacks the manager, password hashes would be useless without the decryption key, which is why sound key management is vital for these apps.
You can use a password management program to keep personal credentials safe or as a means of streamlining and securing the way your employees create, store, and use passwords.
Check out the best enterprise password management solutions on the market and see which one is the best fit for your workforce.
What Are the Common Techniques Used by Hackers to Crack Your Password?
Hackers use numerous techniques to crack passwords. Below is a list of the most common methods a cybercriminal can use to compromise your credentials.
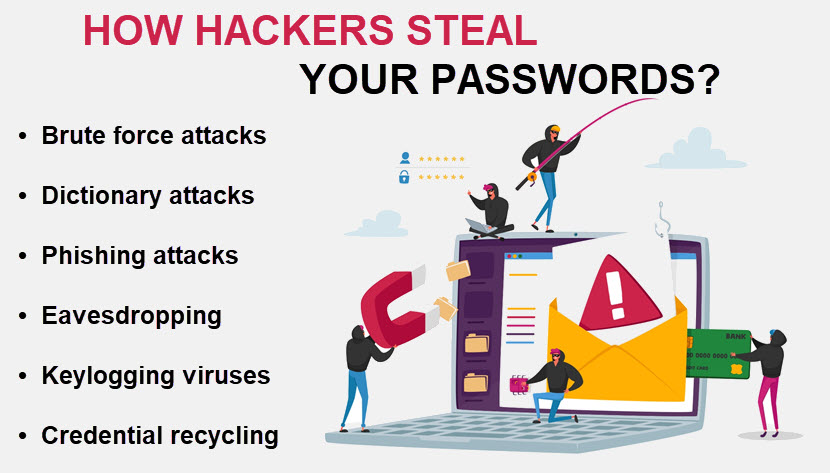
Brute Force Attacks
A brute force attack is a simple process in which a program automatically cycles through different possible combinations until it guesses the target password. These programs can easily crack simple and medium passwords.
An average brute force program can try over 15 million key attempts per second, so 9 minutes is enough to crack most seven-character passphrases. Brute force attacks are the main reason why we insist on a 12-character minimum for passwords.
Learn how to prevent brute force attacks with 8 effective yet easy-to-implement tactics and precautions.
Dictionary Attacks
Whereas a brute force attack tries every possible combination of symbols, numbers, and letters, a dictionary attack tries to crack the password via a prearranged list of words. This attack typically starts with common categories of words, such as:
- Sports teams.
- Names of celebrities, family members, friends, pets, TV/film characters, etc.
- Places (countries, cities, landmarks, etc.).
- Hobbies.
- Animal names.
A dictionary attack also tries substituting letters with symbols, such as 1 for an I or @ for an A. This cyberattack is the main reason why no security-aware person should use common words in their password.
Phishing Attacks
A phishing attack happens when a criminal tries to trick or pressure you into unwittingly sharing credentials. This social engineering threat often relies on emails: hackers send an email pretending to be someone else and refer users to fake login pages.
For example, you (or one of your employees) can receive an email detailing a problem with your credit card account. The email directs to a link that leads to a login page on a phony website resembling your credit card company. If the victim falls for the trick, the hacker who created the false website receives the credentials on a silver platter.
Eavesdropping
A hacker can intercept credentials when victims exchange passwords via unsecured network communications (without VPN and in-transit encryption). Also known as sniffing or snooping, eavesdropping allows a hacker to steal a password without the victim noticing something is wrong.
Keylogging Viruses
A keylogging virus watches every keyboard press you make, enabling a hacker to record your passwords (among other activities).
Dridex and Zeus are the two most common keylogging viruses. Both malicious programs spread through infected email attachments and primarily look for banking login details. To avoid these viruses, you should:
- Know how to identify phishing emails.
- Keep your computer software up to date.
- Install and use a robust anti-virus tool.
- Avoid questionable websites and software.
Think Dridex and Zeus are bad? Wait until you read about the most dangerous ransomware examples and their impact on businesses around the globe.
Credential Recycling
Credential recycling is a less targeted attack but still dangerous to people without a strong password. This tactic uses usernames and passwords collected in other breaches and tries them on as many random platforms and websites as possible.
Hackers typically gather tens of thousands of different credentials leaked from another hack. Unfortunately, as many people use the same simple passwords, this method is very effective. Another name for credential recycling is password spraying.
Do Not Take Any Chances with Your Passwords
If someone steals or guesses your password, that person can easily bypass all other security measures protecting your data. The strong password ideas in this article can help keep you safe and ensure your passphrases never ends up in the wrong hands.



