Data breaches are a major threat to businesses of all sizes, regardless of industry, location, or reputation. If an organization suffers a data breach, the consequences range from costly fines and settlements to long-term brand damage, loss of customers, and, in extreme cases, going out of business.
This article is an introduction to data breaches and the most common attack vectors hackers rely on to compromise sensitive files. We also offer advice on how to prevent data breaches, so read on to see what steps you can take to protect your business from breach attempts.

Data Breach Definition
A data breach is a security incident in which an unauthorized person accesses, steals, copies, or discloses protected data without the data holder's permission or knowledge. A data breach includes both instances in which:
- Someone outside of the company accesses sensitive data.
- An insider threat (employee, contractor, partner, etc.) accesses or copies data without permission.
Data breaches are a threat to any organization, from small and medium businesses to major corporations and government entities. While criminals will go after anyone they deem vulnerable, hackers typically prioritize targeting businesses that keep:
- Personally identifiable info (PII) that can help someone identify, contact, or impersonate an individual.
- Personal health info (PHI) that relates to someone's past, present, or future physical or mental health.
- Confidential business data (trade secrets, contracts, customer lists, business plans, emails, meeting recordings, agreements, etc.).
- Intellectual property (designs, patents, source code, blueprints, etc.).
- Financial data (invoices, credit card numbers, bank details, tax forms, financial statements, etc.).
In 2021, the average cost of suffering a data breach was $4.24 million, a 10% rise from the stats in 2020. The financial penalty typically comes from fines and lawsuits following a breach, but the victim also often suffers long-term reputation hits and can even lose the right to operate in specific regions or sectors.
If the $4.24 million figure did not concern you enough, our article on data breach statistics presents a range of other numbers that demonstrate the true impact a data breach can have on an organization.
How Do Data Breaches Happen?
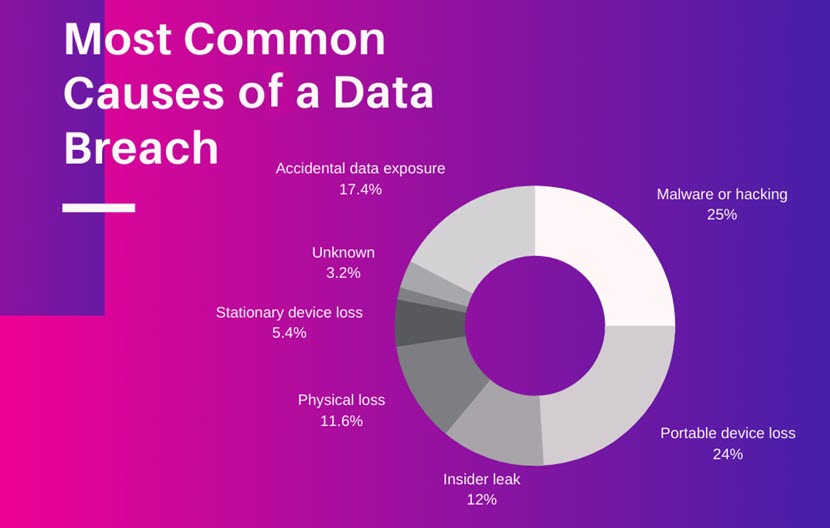
In most cases, the cause of a data breach is either a security vulnerability, protocol loophole, or human error. Statistically, most data breaches occur because of malware or hacking (25%), but other noteworthy causes include:
- The loss of a portable device with sensitive data (24%).
- An insider leak (12%).
- Accidental data exposure, either due to a mistake or negligence (17.4%).
- Physical loss of files or documents (11.6%).
- The loss or theft of a stationary device (5.4%).
- Payment card fraud (1.4%).
A small percentage of data breaches (around 3.2%) have an unknown cause. While some companies prefer not to disclose the way someone compromised their files, others have no idea what caused the breach.
Below are some of the most common scenarios that can lead to a data breach:
- The lack of strong passwords that enables a hacker to crack an employee's credentials.
- An employee opening a malicious email link that installs malware on a company device.
- An unpatched program that allows a hacker to install a backdoor on a system.
- Someone accidentally granting access rights to the wrong person.
- An employee losing a laptop that has no at-rest encryption.
- A disgruntled insider or an ex-employee sharing data with the intent to harm the company.
- An employee using a co-worker's workstation to read or edit files without permission.
- A worker connecting a BYOD device with sensitive data to an unsafe public Wi-Fi.
- A hacker using credential stuffing and exploiting the lack of 2FA to log into an employee account.
- A malicious actor leveraging a misconfigured web or app server to install malware.
Data breaches and leaks often overlap in causes and consequences. Our article on data leakage explains how to protect your company from both accidental and intentional leaks.
Data Breach Methods
A hacker behind a data breach can use various techniques to exploit overlooks in tech and uncareful user behavior. Some of the most common tactics are:
- Phishing: Phishing is a social engineering tactic that aims to fool the victim into clicking a malicious link or sharing sensitive info. Emails are the most usual attack vector for phishing, but in-person and over-the-phone attempts to trick employees are also common.
- Brute force attacks: Hackers use a brute force attack to guess the victim's password (either from scratch or with some knowledge about the target's name, job role, family or pet names, etc.). A top-tier tool can crack a simple password in less than a second, which is why brute force prevention is a priority for any security-aware team.
- Malware: If a hacker installs malware on a company device or server (e.g., via a drive-by download, out-of-date software, or SQL injection), the criminal can create a permanent entry point into the system.
- Spyware: Spyware is a piece of software that can silently gather info about a person or organization and send the data to the hacker without alerting the security team.
- Third-party weaknesses: Even if you successfully secure your local network, a hacker can go after a third-party partner (e.g., a colocation or cloud provider) with weaker security measures.
- Physical theft: Stealing devices to access data is another common tactic. Many data breaches that start with physical theft are opportunistic and involve an employee losing the device before the laptop, USB, or mobile phone with vital data falls into the wrong hands.
- Skimming: Skimmer programs collect payment card data at a point of sale (POS) device or website.
Want to learn more about online risks? Our article on cyber security attack types outlines the 17 most prominent online threats to your company.
Data Breach Stages
Each data breach is a unique incident, but most attacks follow a similar pattern. Below is a step-by-step look at each stage of an average data breach coming from outside the victim's organization.
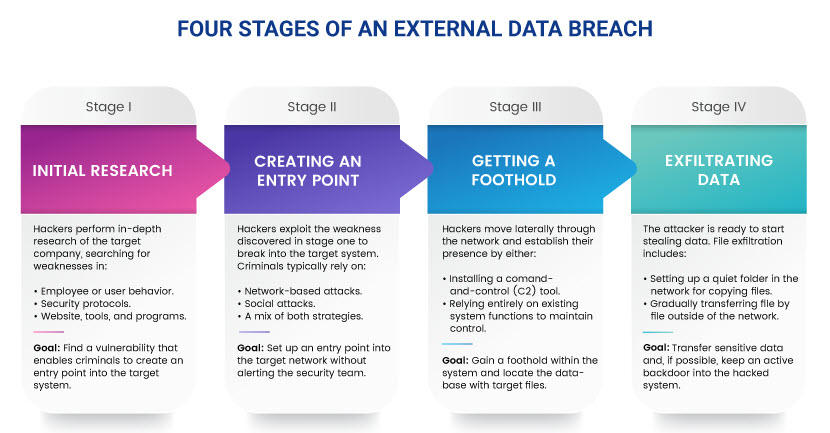
Stage 1: Initial Research
Unless the breach happens due to an opportunistic event (such as someone losing a mobile phone or sending an email to a wrong address), hackers start the attack with in-depth research of the target. The criminals try to gather as much helpful info about the company as possible, which typically involves:
- Probing network ports for exploitable vulnerabilities.
- Investigating the company's toolchain and searching for missing updates.
- Looking for vulnerabilities in the target's code.
- Collecting online info about relevant employees (personal data is useful for cracking passwords and contacts help prepare phishing strategies).
- Testing employee susceptibility to phishing campaigns.
- Observing everyday behavior (online or in-person) for mistakes in protocols.
- Running a few basic attacks to see how well and how quickly the security team responds.
- Gathering general info (who reviews emails, how quickly do the replies come, if certain times of month come with more pressure on employees than others, are there any third-party partners, are employees active on social media, etc.).
Once hackers know the target's weak points, they develop a strategy for creating an initial entry point into the network.
Stage 2: Creating an Entry Point
The tools and techniques a hacker uses at this stage depend on the info the criminal gathered in step one. Most strategies rely on trying to:
- Acquire someone's login credentials.
- Infect the system with malware.
Depending on the strategy, we can classify this stage of a data breach into two categories:
- Network-based attacks.
- Social attacks.
In a network-based attack, a hacker exploits a vulnerability in the target's toolset or network infrastructure. Some of the most common exploits include:
- SQL injections.
- Firewall exploits.
- Session hijacking.
- UPnP weaknesses.
- Bugs in cloud storage integration.
In a social attack, the attacker tries to trick an employee to gain access into the target network. While some social attacks try to get an intruder on-premises, most social breaches start with a phishing email that tricks the reader into clicking a malware-infected link or attachment.
Learn about spear phishing, a highly targeted phishing attack that relies less on spam and more on personalized messages intended for a specific employee.

Stage 3: Establishing a Foothold
Once a hacker has an entry point into the target system, the criminal aims to:
- Gather additional info about the victim.
- Move laterally through the network to find target data.
- Look for privilege escalation opportunities.
Hackers must keep their presence a secret during these activities, which is why most skilled criminals try to cover their actions by:
- Strategically altering the system's security features.
- Launching remote access tools (RATs).
- Creating new system accounts.
- Using diversions such as a novice-level DDoS attack that has nothing to do with the ongoing data breach.
Typically, a criminal tries to gain system control for as long as possible, which is why command-and-control (C2) tools are a common choice at this stage. However, some hackers can use so-called "living off the land" strategies that rely entirely on existing system functions to maintain local control.
Once a hacker controls the system, the goal is to locate target data and, if there is no plan already, figure out how to steal the files most effectively.
Keeping intruders out of your system starts with a safe hosting infrastructure. Our Bare Metal Servers come with built-in high levels of security and offer various automation features that keep deployments safe, repeatable, and non-exploitable.
Stage 4: Going After Data
The most common goal of this stage is data exfiltration (also known as data extrusion or exportation), a process that is notoriously difficult to detect as it often resembles usual network traffic. During exfiltration, the hacker:
- Gradually copies target data into a separate, hidden folder on the system.
- Transfers files outside the victim network, typically in small increments to avoid detection.
DDoS-based distractions are also common during exfiltration as the hacker tries to divert the security team's attention. After the unauthorized data transfer happens, the hacker has successfully stolen files and can sell files to the highest bidder.
Sometimes, the victim does not find out about the data breach even after the hacker steals data. In that case, the criminal often attempts to set up an advanced persistent threat (APT) within the network to stay up to date with the latest files.
Some hackers do not aim to exfiltrate data and instead look to encrypt sensitive files before demanding a ransom for the decryption key. These breaches are known as ransomware and are among the most common and costly cyberattacks a company can encounter.
Our article on ransomware examples explains the diverse ways hackers encrypt sensitive data. You can also check out our ransomware protection guide to learn how best to keep your business safe against this cyber threat.
Data Breach Examples
The table below examines some of the most devastating data breaches in the last ten years, the reason each incident occurred, and the approximate number of records hackers managed to steal.
| Date | Target organization | Number of compromised records | Data breach method |
|---|---|---|---|
| August 2013 | Yahoo | 3,000,000,000 | A phishing scheme |
| November 2019 | Alibaba | 1,100,000,000 | Custom crawler software |
| June 2021 | 1,000,000,000 | Data scraping techniques | |
| April 2019 | 500,000,000 | Data scraping | |
| October 2016 | Adult Friend Finder | 412,000,000 | Poor security practices |
| May 2016 | MySpace | 360,000,000 | Exploit of a security flaw |
| June 2012 | 165,000,000 | A weakness in the blog page | |
| October 2013 | Adobe | 153,000,000 | Raid on a backup server |
| February 2018 | Under Armour (MyFitnessPal app) | 150,000,000 | Unconfirmed (suspected security vulnerability or actions of an employee) |
| May-July 2017 | Equifax | 145,500,000 | A vulnerability within the dispute portal servers |
| May 2014 | eBay | 145,000,000 | Stolen employee log-in credentials |
| December 2013 | Target | 110,000,000 | Stolen credentials of a third-party vendor |
| April 2011 | Sony PlayStation Network | 102,000,000 | Exploit of a security flaw |
| October 2017 | MyHeritage | 92,000,000 | Poor security practices |
| July 2014 | JP Morgan & Chase | 83,000,000 | A phishing scheme |
| February 2015 | Anthem | 79,000,000 | Spear phishing emails and backdoor malware |
Data Breach Prevention - Best Practices
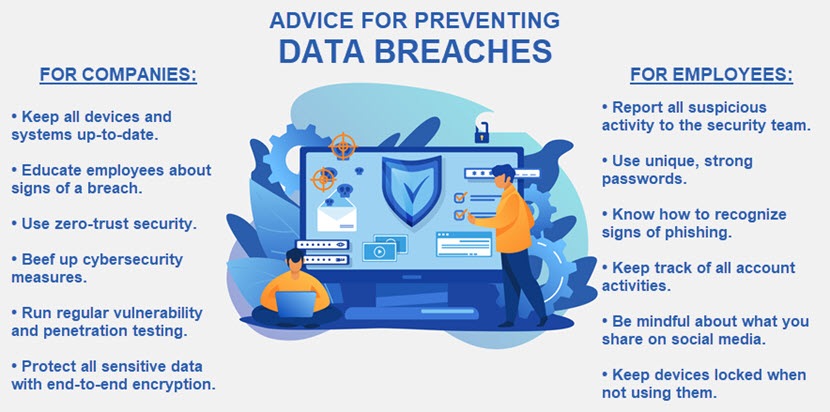
While you cannot stop a hacker from attempting to cause a data breach, you can adopt best practices that help ensure criminals do not succeed in their attempts. Here is some advice for protecting yourself from data breaches:
- Keep all devices, systems, and networks up to date with the latest patches to prevent exploits of outdated software.
- Organize cybersecurity awareness training to educate employees about social engineering tactics and teach workers how to act if they detect suspicious activity.
- Improve cybersecurity by deploying intrusion detection systems (IDS), robust firewalls, anti-virus and malware programs, cloud security policies, VPNs, endpoint threat detection, and cyber kill chains.
- Use zero trust security and network segmentation to prevent an intruder from easily moving between internal systems.
- Enforce the use of strong passwords unique for each account and ensure employees update passphrases regularly.
- Create a disaster recovery plan and use data backups to ensure the firm can quickly recover from a breach attempt.
- Run regular vulnerability assessments and penetration tests to inspect your system's resilience to different data breach tactics.
- Rely on end-to-end encryption and careful key management to ensure a hacker cannot decipher data even if they reach its database.
Ready to capitalize on the security benefits of encryption? Our encryption management platform centralizes all key-related tasks and enables you to manage your encryption strategy from a single pane of glass.
Data Breaches Should be a Security Team's Top Concern
At the very least, a successful data breach can cause brand damage and hurt the bottom line. At worst, this incident can lead to costly legal trouble and be the first step to going out of business. Prevention is the key to stopping breaches, so ensure the security team proactively protects sensitive files to keep the company out of the financial mess caused by a full-blown data breach.



