This article is an introduction to network security. Read on to learn the value of secure networks and see what tactics companies use to keep intruders away from data and resources.
What is Meant by Network Security?
Network security is a set of hardware and software solutions that stop unauthorized users from accessing a network and its resources. The goal of network security is to create a safe work platform for devices, users, and programs.
Network security has several vital roles within an IT environment:
- Prevent unauthorized access to assets and data.
- Protect network data, infrastructure, and all traffic from external threats.
- Stop threats from spreading through the system.
- Enable secure data sharing between systems and employees.
- Grant users adequate access to resources.
- Detect and respond to suspicious user behavior and software anomalies.
The framework for successful network security has three phases:
- Protection: Configure systems and networks correctly and ensure there are no vulnerabilities.
- Detection: Identify dangers before the attacker does damage or spreads through the network.
- Reaction: Quickly eliminate threats and return the network to a safe state.
Setting up and managing network security is a complicated and time-consuming task. Admins typically rely on network security management tools to better monitor activity and speed up response times. Standard network security tools include:
- Packet sniffers that give insight into data traffic.
- Vulnerability assessment scanning tools.
- Intrusion detection and prevention software.
- SIEM tools that analyze network data.
- Penetration testing software.
Use penetration testing tools to check your network for potential weak points.
How Network Security Works?
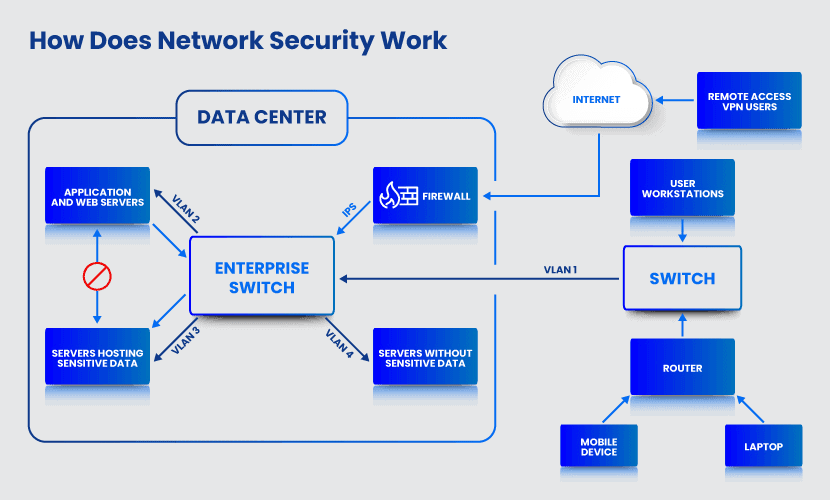
Network security revolves around two main processes: authentication and authorization. Authentication is the practice of checking the user’s identity before granting access to a system. A network can verify the user in three different ways:
- One-factor authentication: A user types in a username and password to log in.
- Two-factor authentication: A user provides a username and a password, but the network requires further verification. Systems typically ask for something that the user possesses, such as a security token, a credit card, or a mobile phone.
- Three-factor authentication: A network requires two-factor authentication plus biometric recognition such as a voice, fingerprint, or retinal scan. This and other security techniques are used to secure data centers.
Learn about Kerberos authentication, the most reliable computer-network verification protocol.
Once the network verifies the identity, the user logs in. Authorization then determines the level of access based on network policies.
While useful for preventing unauthorized access, authentication and authorization do not check network traffic for harmful content. A firewall prevents malicious traffic from entering the network. Anti-virus software and intrusion prevention systems (IPS) recognize malicious activity within the network. Some companies also use machine learning and behavioral analytics to analyze traffic and detect active dangers.
Check out Data Security Cloud if you are looking for an out-of-the-box cloud solution that adheres to strict security regulations.
Network Security Controls
Network security consists of three different controls: physical, technical and administrative.
Physical Network Security
Physical security controls prevent unauthorized staff and intruders from physically reaching network components. This type of security control protects routers, cabling cupboards, computers, dedicated servers, etc. Locks, security cameras, fences, and guards are standard methods of physical network security.
Besides protecting static equipment, physical network security also must stop the theft of employee hardware. Portable devices are easy targets, so preventing thieves from stealing and extracting data from hardware is essential.
Technical Network Security
Technical security controls protect network data and systems. This type of security keeps both stored and in-transit data safe. Technical security controls protect data and systems both from unauthorized third parties and malicious insiders.
Administrative Network Security
Administrative security controls consist of policies and processes that monitor user behavior. This type of control defines:
- How user authentication works.
- Each user’s level of access.
- How IT staff makes changes to the network infrastructure.
What Are the Types of Network Security?
Security experts use various techniques and strategies to keep a network safe. Here are the most effective types of network security:
- Anti-virus and anti-malware software: Prevent, detect, and remove software viruses and malware trying to compromise the network.
- Application security: Protect applications from exploitable weaknesses by testing features, keeping tools up to date, and removing compatibility issues.
- Data loss prevention (DLP): Data loss prevention tools detect and stop unauthorized data flows.
- Email security: Email security protects employees’ inboxes, the primary source of malware, spam, and phishing threats.
- Endpoint security: Ensure endpoints such as desktops, laptops, and mobile devices do not become an entry point for malicious actors and programs.
- Firewall: Firewalls are barriers between internal and external networks that scan for and stop dangerous content from entering the system.
- Mobile device security: Protect data stored on and transmitted by phones, tablets, wearables, and other portable devices.
- Network monitoring and detection systems: Monitor network traffic and automatically respond to suspicious activity.
- Virtual Private Networks (VPN): Ensure secure remote access for employees with virtual private networks.
- Web security: Protect a network by proactively detecting and removing web-based threats.
Our article about types of network security provides an in-depth explanation of the different methods companies use to keep networks safe.
While network security requires the use of various technologies, the protection strategy must be holistic. Poor integrations and lack of compatibility between components create weak points hackers can exploit to breach the system.
Why is Network Security Important?
Network security enables an organization to deliver products and services safely and consistently. This type of protection is the first line of defense against all significant cyber threats:
- Distributed denial-of-service (DDoS): DDoS attacks slow down or deny services by overwhelming a network with fake spikes in traffic.
- Malware: Malware infections include different types of ransomware (programs that encrypt data and demand ransoms), worms (malware that quickly replicates through a network), and spyware (programs that allow an attacker to track user activities).
- Insider attacks: Insider threats occur when employees either accidentally or intentionally damage the network or leak data.
- Advanced Persistent Threats (APT): An APT attack is a dangerous cyber threat that typically starts with a compromised network.
- Vulnerability exploits: Attackers target weak points in login portals, applications, devices, or other areas to penetrate a network.
Learn about different enetwork security threats and start preparing your systems for potential attacks.
Network security also enables a company to:
- Boost network performance and reliability.
- Reduce overhead expenses.
- Prevent costly downtime.
- Ensure compliance with relevant regulations and laws.
- Build trust with business partners and end-users.
- Enhance the longevity of devices.
How to Improve Network Security?
Regular Auditing and Mapping
An administrator must have a clear understanding of the network infrastructure to set up proper defenses. Always know the models, locations, and configurations of:
- Firewalls.
- Routers.
- Switches.
- Cabling.
- Ports.
- Wireless access points.
An admin must also know all connected devices (servers, computers, printers, etc.) and their connectivity path through the network.
Auditing and mapping help identify potential weak points and ways to improve network safety, performance, and reliability.
Perform a network security audit to get an in-depth analysis of your current defenses.
Segment the Network
Network segmentation breaks a network up into smaller subsystems. Each subnetwork operates as an independent system with separate security controls and access rules.
Segmenting a network prevents an attacker from moving freely through the system. If a hacker breaches a part of a network, other segments are not automatically in danger.
Use Strong Passwords
Poor password choices create dangerous security gaps. Weak passwords make brute force attacks easier, heighten the threat of malicious insiders, and enable an attacker to silently gain network access.
Ensure employees use complex and unique passwords and that they change them every few weeks. Also, educate the staff about the importance of not sharing passwords with other employees.
Consider using an enterprise password management solution to streamline password practices.
Build Staff Awareness
Ensure employees know their roles and responsibilities in keeping the network safe. Careful employees are a vital line of defense, so train your staff to:
- Recognize signs of social engineering.
- Not click links in pop-ups and strange emails to avoid phishing attacks.
- Connect only to secure Wi-Fi networks.
- Never turn off firewalls and anti-virus software.
- Delete old accounts they no longer use.
- Respect network security practices.
- Turn off their computers and laptops when they are not in use.
- Quickly communicate with the security team if something goes wrong.
You should also ensure all workers know about and have access to security policies.
Keep Software Up to Date
All network software must have the latest updates to defend against the latest threats properly. Consider investing in a patch management system that keeps all your network software up to date.
Zero Trust
Use Zero Trust security to restrict user access to valuable data. Users should have only as much access as they require to perform their jobs.
Zero Trust protects a network and its data from outside and inside dangers. This policy also helps companies comply with data privacy and security laws (FISMA, HIPAA, PCI, GDPR, CCPA, etc.).
Set Up Honeypots
Honeypots are fake subnetworks or data storages that security teams deploy as decoys. These network segments have intentional flaws that attract attackers. Regular users do not access honeypots, so any activity in that network area is an indicator of third-party presence.
Honeypots enable a security team to:
- Quickly identify intruder activity.
- Analyze malicious tactics and patterns.
- Identify weak points in the network.
- Distract hackers from real servers and resources.
A Foundation for Successful IT
Network security reduces the risk of cyber threats and is essential to safe IT operations. Improve your network’s safety to enable teams to grow and work without unnecessary setbacks and costly downtime. Consider checking our article on Network Infrastructure Security to learn more about the prerequisites for efficient business communication, productive teams, and safe operations.



