In this article you will learn:
- Understand what a Security Operations Center is and active how detection and response prevent data breaches.
- Six pillars of modern security operations you can’t afford to overlook.
- The eight forward-thinking SOC best practices to keep an eye on the future of cybersecurity. Including an overview and comparison of current Framework Models.
- Discover why your organization needs to implement a security program based on advanced threat intelligence.
- In-house or outsource to a managed security provider? We help you decide.
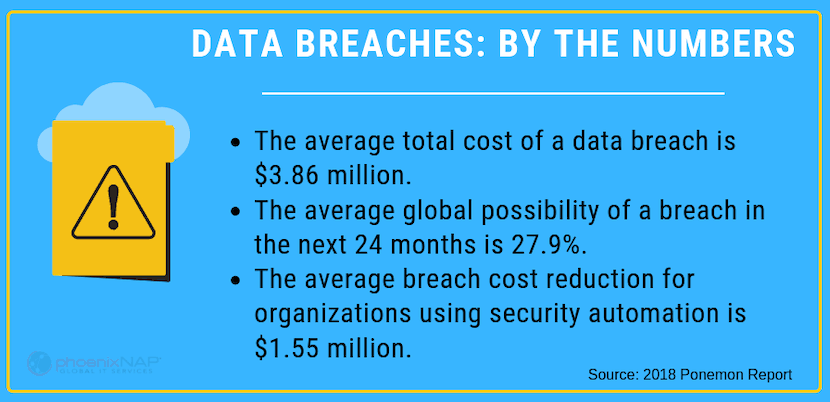
The average total cost of a data breach in 2018 was $3.86 million. As businesses grow increasingly reliant on technology, cybersecurity is becoming a more critical concern.
Cloud security can be a challenge, particularly for small to medium-sized businesses that don’t have a dedicated security team on-staff. The good news is that there is a viable option available for companies looking for a better way to manage security risks – security operations centers (SOCs).
In this article, we’ll take a closer look at what SOCs are, the benefits that they offer. We will also take a look at how businesses of all sizes can take advantage of SOCs for data protection.
What is a Security Operations Center?
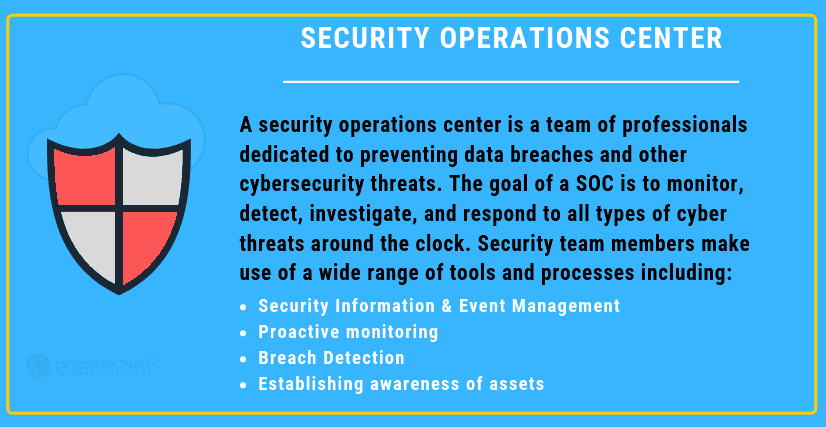
A security operations center is a team of cybersecurity professionals dedicated to preventing data breaches and other cybersecurity threats. The goal of a SOC is to monitor, detect, investigate, and respond to all types of cyber threats around the clock.
Team members make use of a wide range of technological solutions and processes. These include security information and event management systems (SIEM), firewalls, breach detection, intrusion detection, and probes. SOCs have many tools to continuously perform vulnerability scans of a network for threats and weaknesses and address those threats and deficiencies before they turn into a severe issue.
It may help to think of a SOC as an IT department that is focused solely on security as opposed to network maintenance and other IT tasks.
6 Pillars of Modern SOC Operations
Companies can choose to build a security operations center in-house or outsource to an MSSP or managed security service providers that offer SOC services. For small to medium-sized businesses that lack resources to develop their own detection and response team, outsourcing to a SOC service provider is often the most cost-effective option.
Through the six pillars of security operations, you can develop a comprehensive approach to cybersecurity.
- Establishing Asset AwarenessThe first objective is asset discovery. The tools, technologies, hardware, and software that make up these assets may differ from company to company, and it is vital for the team to develop a thorough awareness of the assets that they have available for identifying and preventing security issues.
- Preventive Security MonitoringWhen it comes to cybersecurity, prevention is always going to be more effective than reaction. Rather than responding to threats as they happen, a SOC will work to monitor a network around-the-clock. By doing so, they can detect malicious activities and prevent them before they can cause any severe damage.
- Keeping Records of Activity and CommunicationsIn the event of a security incident, soc analysts need to be able to retrace activity and communications on a network to find out what went wrong. To do this, the team is tasked detailed log management of all the activity and communications that take place on a network.

- Ranking Security AlertsWhen security incidents do occur, the incident response team works to triage the severity. This enables a SOC to prioritize their focus on preventing and responding to security alerts that are especially serious or dangerous to the business.
- Modifying DefensesEffective cybersecurity is a process of continuous improvement. To keep up with the ever-changing landscape of cyber threats, a security operations center works to continually adapt and modify a network’s defenses on an ongoing, as-needed basis.
- Maintaining ComplianceIn 2019, there are more compliance regulations and mandatory protective measures regarding cybersecurity than ever before. In addition to threat management, a security operations center also must protect the business from legal trouble. This is done by ensuring that they are always compliant with the latest security regulations.
Security Operations Center Best Practices
As you go about building a SOC for your organization, it is essential to keep an eye on what the future of cybersecurity holds in store. Doing so allows you to develop practices that will secure the future.
SOC Best Practices Include:
Widening the Focus of Information Security
Cloud computing has given rise to a wide range of new cloud-based processes. It has also dramatically expanded the virtual infrastructure of most organizations. At the same time, other technological advancements such as the internet of things have become more prevalent. This means that organizations are more connected to the cloud than ever before. However, it also means that they are more exposed to threats than ever before. As you go about building a SOC, it is crucial to widen the scope of cybersecurity to continually secure new processes and technologies as they come into use.
Expanding Data Intake
When it comes to cybersecurity, collecting data can often prove incredibly valuable. Gathering data on security incidents enables a security operations center to put those incidents into the proper context. It also allows them to identify the source of the problem better. Moving forward, an increased focus on collecting more data and organizing it in a meaningful way will be critical for SOCs.
Improved Data Analysis
Collecting more data is only valuable if you can thoroughly analyze it and draw conclusions from it. Therefore, an essential SOC best practice to implement is a more in-depth and more comprehensive analysis of the data that you have available. Focusing on better data security analysis will empower your SOC team to make more informed decisions regarding the security of your network.
Take Advantage of Security Automation
Cybersecurity is becoming increasingly automated. Taking DevSecOps best practices to complete more tedious and time-consuming security tasks free up your team to focus all of their time and energy on other, more critical tasks. As cybersecurity automation continues to advance, organizations need to focus on building SOCs that are designed to take advantage of the benefits that automation offers.
Security Operations Center Roles and Responsibilities
A security operations center is made up of a number of individual team members. Each team member has unique duties. The specific team members that comprise the incident response team may vary. Common positions – along with their roles and responsibilities – that you will find in a security team include:
- SOC ManagerThe manager is the head of the team. They are responsible for managing the team, setting budgets and agendas, and reporting to executive managers within the organization.
- Security AnalystA security analyst is responsible for organizing and interpreting security data from SOC report or audit. Also, providing real-time risk management, vulnerability assessment, and security intelligence provide insights into the state of the organization’s preparedness.
- Forensic InvestigatorIn the event of an incident, the forensic investigator is responsible for analyzing the incident to collect data, evidence, and behavior analytics.
- Incident ResponderIncident responders are the first to be notified when security alerts happen. They are then responsible for performing an initial evaluation and threat assessment of the alert.
- Compliance AuditorThe compliance auditor is responsible for ensuring that all processes carried out by the team are done so in a way that complies with regulatory standards.
SOC Organizational Models
Not all SOCs are structured under the same organizational model. Security operations center processes and procedures vary based on many factors, including your unique security needs.
Organizational models of security operations centers include:
-
Internal SOC
An internal SOC is an in-house team comprised of security and IT professionals who work within the organization. Internal team members can be spread throughout other departments. They can also comprise their own department dedicated to security. -
Internal Virtual SOC
An internal virtual SOC is comprised of part-time security professionals who work remotely. Team members are primarily responsible for reacting to security threats when they receive an alert. -
Co-Managed SOC
A co-managed SOC is a team of security professionals who work alongside a third-party cybersecurity service provider. This organizational model essentially combines a semi-dedicated in-house team with a third-party SOC service provider for a co-managed approach to cybersecurity. -
Command SOC
Command SOCs are responsible for overseeing and coordinating other SOCs within the organization. They are typically only found in organizations large enough to have multiple in-house SOCs. -
Fusion SOC
A fusion SOC is designed to oversee the efforts of the organization’s larger IT team. Their objective is to guide and assist the IT team on matters of security. -
Outsourced Virtual SOC
An outsourced virtual SOC is made up of team members that work remotely. Rather than working directly for the organization, though, an outsourced virtual SOC is a third-party service. Outsourced virtual SOCs provide security services to organizations that do not have an in-house security operations center team on-staff.
Take Advantage of the Benefits Offered by a SOC
Faced with ever-changing security threats, the security offered by a security operations center is one of the most beneficial avenues that organizations have available. Having a team of dedicated information security professionals monitoring your network, security threat detection, and working to bolster your defenses can go a long way toward keeping your sensitive data secure.
If you would like to learn more about the benefits offered by a security operations center team and the options that are available for your organization, we invite you to contact us today.
For your next read, we suggest checking out what is SecOps.