Are your company executives vulnerable to an attack?
A whaling attack is very similar to a phishing attack, just with bigger targets such as the c-suite. In this article, learn how to stay ahead of the threat and prevent a data breach.
What is a Whaling Attack?
A whaling attack is a spear phishing attack against a high-level executive. This is usually a C-level employee, like a Chief Executive or Chief Financial Officer.
In this attack, the hacker attempts to manipulate the target. The goal might be high-value money transfers or trade secrets. The term whaling (or whale phishing) refers to the high value of the target.

Differences Between Phishing, Whaling Phishing, and Spear Phishing
With typical phishing, attackers cast a wide net. This often means spamming a mailing list. Only a fraction of recipients needs to respond to make it worthwhile. Regular phishing attacks often ask the target for money and promise to repay more money later. The attacker then takes the money and vanishes.
A spear phishing attack is slightly different. In this type of phishing attack, the attacker identifies a specific target. Hackers learn details about their target and tailor the attack accordingly. A spear phisher might select a person in the IT department of a major corporation. Then learn that person’s habits, likes, and dislikes to use that knowledge for gaining trust. The attacker can then use social engineering against the target. The victim may grant access to sensitive data or even transfer money.
Spear phishing attacks target are regular everyday people. A whaling attack is targeting a high-level or difficult target. This is usually a C-level employee of a corporation. These targets often have better security awareness. A whaler is usually after large money transfers or trade secrets.
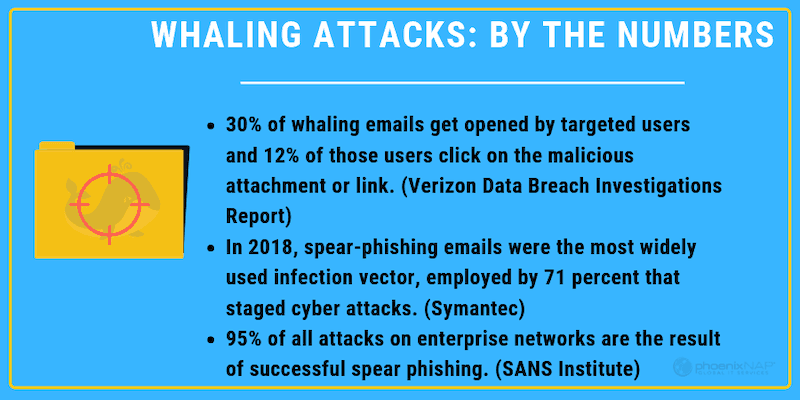
How Whale Phishing Works
- Urgency: One common phishing tactic is to create a sense of urgency. Whaling attacks are no different. Whaling attacks usually imply massive consequences and a short time frame. Urgency discourages the target from taking time to consider their actions.
- High risk / low effort: The attacker may threaten a costly lawsuit or public relations exposure. These threats would be disastrous to the company or individual. The hacker wants the target to bypass the security procedure. Usually, the action is simple compared to the danger. One example might be wiring funds to avoid regulatory action. Another might be clicking a link to a website that installs malware. This attack uses a substantial threat to get a low-effort response.
- Specific details: Whaling attacks can yield high rewards. Attackers spend substantial time and effort on the attack. Social engineering is often used to obtain personal information. They research the company to learn the names and achievements of different employees and use the details to exploit the target’s trust. If the target trusts the attacker, they are more likely to comply.
- Impersonation: Another common tactic is the use of impersonation. A hacker can use details from the corporation to impersonate a higher official. For example, an attacker might pose as a senior manager and ask for an employee payroll report. Or, they may pretend to be a fellow employee known by the target. Often, the email address is spoofed – or faked – to look authentic. Spoofing can include a valid-looking email address and company logos.
How to Prevent Whale Phishing
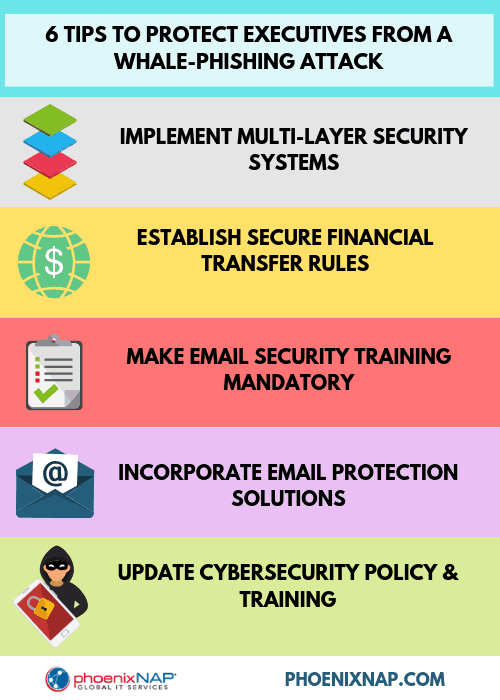
Educate employees in sensitive positions
This includes all of senior management. It’s also wise to educate employees in sensitive positions like IT and accounting. Employees in executive positions also make tempting targets. Train ALL employees to be wary of phishing and whaling attacks. If employees know what to watch for, they can protect themselves.
Senior employees should have private social media profiles
Social media sites provide a wealth of information for social engineering. An attacker might learn that an executive burned the hamburgers at a company picnic, then use that information to build credibility. Keeping profiles private helps limit an attacker’s ability to find compromising data.
Flag emails from outside the company
Whaling attacks often impersonate someone from within the company. Flagging external emails can warn users that the attacker is not who they claim to be. Attackers rarely attack from within the same company. This strategy can raise awareness of an attack.
Practice and enforce good email hygiene
Users should not click suspicious links or unsolicited attachments.
If the employee didn’t specifically request the email, they should take extra care. Anything that requires immediate and drastic action should be verified. Scan emails with a virus and malware scanner. Hover a mouse pointer over the sender’s name to see the real email address. In a web-based email, click the “more information” or “show details” to see the sender.
Use a system of verification for drastic action
Security awareness training is key. Train your staff on data security procedures, and how to check for suspicious phishing emails. Instruct sensitive employees to verify unusual requests.
For example, an employee might check the threat of a lawsuit with the legal department. Or, they might call a senior manager on the phone to verify the transfer of employee tax records. Consider a policy that requires verification for wire transfers.
Use data protection technologies
People make mistakes, and hackers are specialists in social engineering. As a last resort, implement data practices that make it difficult for one individual to cause damage.
Use access management, make sure root user access is limited to point-of-need. Also, make sure all user permissions are appropriate and necessary for each job function. Implement and maintain the usual suite of IT security tools: firewalls, intrusion detection software, and malware scanning utilities.
Active Threat Protection Keeps your Business Safe From Whaling
Whaling is a lot like spear phishing – just with bigger fish.
Whaling targets yield much bigger rewards, which creates an incentive to invest more effort into an attack. Though anyone can be vulnerable to social engineering, security training remains the best defense. High-level employees should expect to be a target, and defend themselves accordingly. In the event of a breach, incident response planning can help mitigate damage.
Learn more about targeted cyber threats in our CEO Fraud attack article and how these types of cyber attacks work.