A network breach is an inevitable risk online. Attacks are bound to occur, and every network must be able to withstand a break-in. One cybersecurity mechanism stood out as very effective in limiting the damage in case of a network breach.
That cybersecurity technique is network segmentation.
Network segmentation can protect vital parts of the network during successful data breaches. If the system gets compromised, this defense mechanism limits the damage intruders can cause.
This article presents all the security benefits of network segmentation. You will learn how multi-layer protection can resist attacks and why segmentation is more reliable than flat network structures.
What is Network Segmentation?
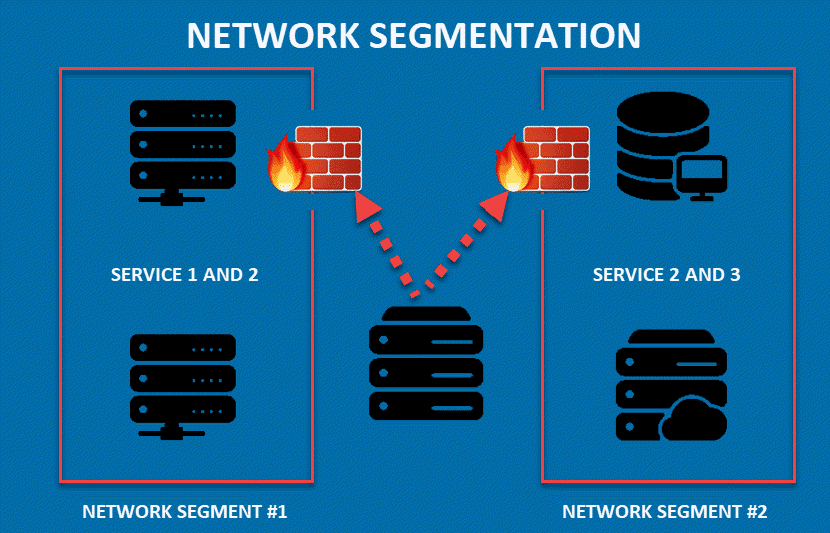
Network segmentation is the process of dividing a network into smaller sections. These sections are created by placing barriers between parts of the system that don’t need to interact. For example, a company may create a subnet for its printers, or make a segment reserved for storing data.
Once you segment a network, every subnet functions as an independent system with unique access and security controls. Such network design allows you to control the flow of data traffic between sections. You can stop all traffic in one segment from reaching another. Additionally, network engineers use network segmentation to filter the data flow by traffic type, source, or purpose.
Isolating parts of a network limits a threat’s ability to move freely through the system. If a section of the network gets breached, other segments are not compromised.
Types of Network Segmentation
Network engineers segment a network either physically or virtually. Let’s compare the two segmentation methods:
- Physical segmentation: To physically segment a network, each subnet needs to have its wiring, connection, and a type of firewall. Physical segmentation offers reliable protection, but it can be hard to apply on a large system.
- Virtual segmentation: This is the more common and affordable method of dividing a network. Different segments share the same firewalls, while switches manage the virtual local area network (VLAN).
Both segmentation methods have their pros and cons, but their effect is the same. You limit communication within the network and make it hard for a threat to attack more than one section.
Why Segment a Network?
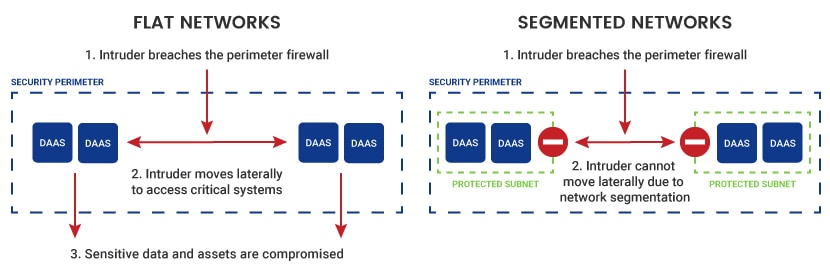
Standard flat networks are simple to manage, but they do not offer reliable protection. Firewalls monitor all incoming traffic in a flat network architecture, and the focus is on stopping attacks from outside the system. If hackers pass the perimeter and enter the network, nothing prevents them from accessing databases and critical systems.
Segmentation eliminates the flaws of flat networks. Segmenting a network also leads to better performance due to less congestion. With fewer hosts per subnet, a segmented network minimizes local traffic and reduces the “noise” in broadcast traffic.
Another benefit of a network segmentation policy is that it helps ease the compliance requirements. You can split a network into zones that contain data with the same compliance rules. Separate zones decrease the scope of compliance and simplify security policies.
Security Advantages of Network Segmentation
Of all the types of network security, segmentation provides the most robust and effective protection.
Network segmentation security benefits include the following:
1. Strong Data Protection
The more you control the traffic in a network, the easier it is to protect essential data. Segmentation builds a wall around your data caches by limiting the number of network sections that access them.
Fewer segments with access to data mean fewer points of access for hackers to steal anything of value. Between limited access and local security protocols, you reduce the risk of data loss and theft.
2. Threat Containment
If hackers breach a segmented network, they are contained within a single subnet. It takes time to break into the rest of the system.
As hackers try to force their way into other subnets, admins have time to upgrade the security of other segments. Once they stop the problem from spreading, admins can turn their attention to the breached section.
phoenixNAP uses network micro-segmentation and machine learning and behavioral analytics in the world’s most secure cloud platform – Data Security Cloud.
3. Limited Access Control
Segmentation protects from insider attacks by limiting user access to a single part of a network. This security measure is known as the Policy of Least Privilege. By ensuring only a select few can reach vital segments of the network, you limit the way hackers can enter critical systems.
The Policy of Least Privilege is vital as people are the weakest link in the network security chain. According to Verizon’s 2020 Data Breaches Report, over two-thirds of malware network breaches happen because of malicious emails.
A segmented network will keep intruders away from critical resources if a user’s credentials are stolen or abused.
4. Improved Monitoring and Threat Detection
Segmentation lets you add more points of network monitoring. More checks make it easier to spot suspicious behavior. Advanced monitoring also helps identify the root and scope of a problem.
Monitoring log events and internal connections enable admins to look for patterns in malicious activity. Knowing how attackers behave allows for a proactive approach to security and helps admins protect high-risk areas.

5. Fast Response Rates
Distinct subnets allow admins to respond to events in the network quickly. When an attack or an error occurs, it is easy to see which segments are affected. These insights help to narrow the focus area of troubleshooting.
Quick responses to events in the network can also improve user experience. Unless a subnet dedicated to users has been breached, customers will not feel the impact of an issue in a segmented network.
6. Damage Control
Network segmentation minimizes the damage caused by a successful cybersecurity attack. By limiting how far an attack can spread, segmentation contains the breach in one subnet and ensures the rest of the network is safe.
Network errors are also contained within a single subnet. The effects of an issue are not felt in other segments, making the error easier to control and fix.
7. Protect Endpoint Devices
Due to constant flow control, segmentation keeps malicious traffic away from unprotected endpoint devices. This benefit of network segmentation is becoming crucial as IoT devices become commonplace.
The endpoint device is both a usual target and starting point of cyberattacks. A segmented network isolates these devices, limiting the risk of exposure for the entire system.

Don’t Overlook The Importance of Network Segmentation
While network segmentation is not a novelty, it is by no means outdated. Between the cut in attack surface and traffic control, segmentation is among the best methods of stopping critical breaches.
Network segmentation is currently more a best practice model than a requirement. However, trends in industries with frequent cyberattacks — most notably the Payment Card Industry — suggest that segmentation could become a mandatory security measure. Whether that happens or not, the demand for subnets in some of the most regulated industries speaks volumes about the security benefits of network segmentation.
If you want to learn more about what it takes to secure a Cloud platform, read our Secure by Design Manifesto and discover how many security layers are necessary to design the most secure Cloud infrastructure in the world.